This series of articles will walk you through the most important topics about security and mobile applications, whatever the platform is (iOS, Android or others).
The objective is to demystify the different aspects of mobile security, in simple words.
This third episode will walk you through vulnerabilities related to data transportation.
A mobile application rarely works offline. An exception would be a dictionary application, which usually works by itself and does not require any communication with a server in order to get its content: the whole data is already contained inside the application, and users choose what word definition to display.
But this is an exception, as most apps exchange data with a web server.
Data exchanged with the mobile app
Depending on the business case, different kinds of data can be sent or received by the mobile app, like:
- Authentication credentials
- User session data
- Personal data (PII)
- Transactional data related to the business case
- Banking data
How data is exchanged
Depending on the case, different data streams might be present within a single application.
Let’s take the example of an e-commerce mobile app allowing users to buy products, and to write comments.
The following data can be transferred to and from the application:
- User authentication data
- Application usage statistics
- Data related to comments left on products
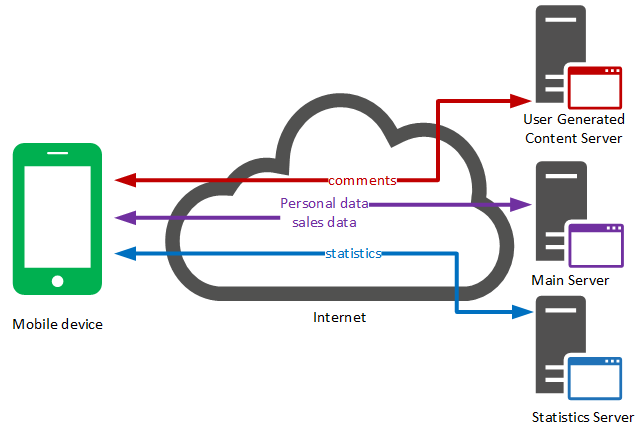
In our example, three different servers interact with the mobile application. Some contain sensitive data, others don’t.
Risks and attacks
Risks on data transfers are various and numerous.
Firstly, not using data encryption like HTTPS (TLS) is still a widespread vulnerability.
We were thus able to observe that several popular applications do not encrypt authentication credentials, for instance.
In this case, an attacker can simply “listen” on the network used by the mobile device, and collect sensitive data.
Spying networks used by mobile devices is very easy, especially since users do not hesitate to connect to public Wi-Fi hotspots.
A recent experimentation conducted by Avast during the Mobile World Congress revealed that many users connect to a Wi-Fi without knowing whether it is safe or not: Within a few hours, more than 2000 people connected to several unsafe public Wi-Fi networks, which were created by Avast.
The experimentation allowed Avast team to spy the traffic in order to simulate a malicious attack and perform tests on captured data. They found that 63% of the networks’ users could have their personal data intercepted.
See the related article on Avast’s website : https://press.avast.com/en-us/avast-wi-fi-hack-experiment-demonstrates-reckless-behavior-of-mobile-world-congress-attendees
This shows that spying internet café Wi-Fi networks or creating fake Wi-Fi networks is really easy.
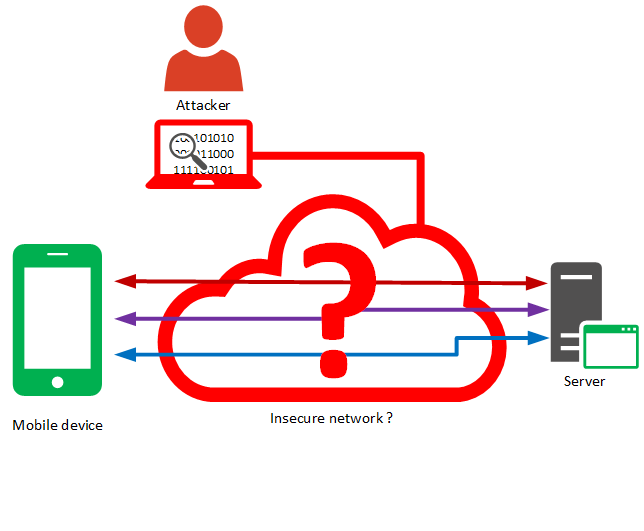
When data is transmitted over HTTPS, remains the question as to whether HTTPS has been properly configured, or not.
In fact, that configuration can be done in various ways, more or less efficiently.
Elements that attackers usually observe are related to:
- Algorithms chosen to implement HTTPS (some of them are weak and can be “broken”)
- The use of expired certificates or self-signed certificates, which do not have any value
- Verifications performed by the mobile application concerning the server it is communicating with
Securing data transfers
One approach to adopt when developing a mobile application and particularly concerning the security of data is not to trust the user’s connection.
Assuming that the connection (Wi-Fi, 3G/4G…) is potentially spied or spoofed.
It then becomes obvious that some verifications must be performed, in order to check which server the mobile app is communicating with, and to properly encrypt data.
Here are some important points and technical solutions to implement:
- Tunnel sensitive data into an HTTPS connection
- Avoid mixing secured / non-secured data, especially on “web” contents
- Verify on the server that only recent and secure algorithms are accepted to establish HTTPS connections
- Use only SSL certificates generated by well-known certificate authorities
- On the mobile app, verify that the server is indeed the one it pretends to be (“certificate pinning”)
- Respect “good practices” dictated by mobile platforms editors (iOS, Android…)
A VPN connection can be considered as a complementary solution, for the most sensitive applications within professional contexts.
A security audit of the mobile application is a good way to detect and then fix its vulnerabilities.
As we can see, the security of data transfers is not automated and requires a special attention from developers.
The mobile application as well as the server have their own roles and responsibilities, to ensure that communications are secured and to reduce the risk of data being compromised.
