This series of articles will walk you through the most important topics about security and mobile applications, whatever the platform is (iOS, Android or others).
The objective is to demystify the different aspects of mobile security, in simple words.
This second episode makes a focus on insecure data storage.
A mobile application may store different types of information:
- Geolocation data
- Transactions
- Credentials or authentication tokens
- Personal Information (PII)
- Application data
- Cached data
How data is stored on the mobile application
Depending on the platform (iOS, Android…), different kinds of data storage can be used. Database, flat files, xml files, Plist files, SD card… different locations for different purposes.
On top of the location, data can be encrypted, more or less efficiently.
Deciding what data is stored on the device is very important. Even if the user can be trusted, a mobile device can be lost or stolen, potentially exposing what is stored in its memory.
Additionally, a device is not necessarily secure, since many users “jailbreak” or “root” them in order to get access to extended functionalities and software. This process removes an important security layer.
Attack example
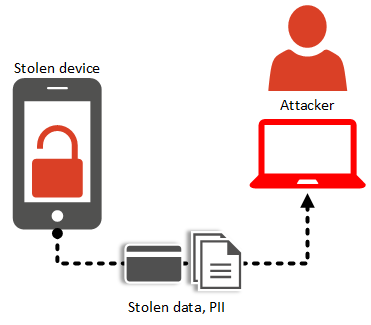
In scenario 1, a user looses his mobile (theft).
The thief is experienced in device hacking and connects the device to his computer, using specific tools that allow access to the memory and files system.
Looking at files located inside the application, the thief finds personal information, as well as credit card information that were stored for future purchases and encrypted with a weak algorithm.
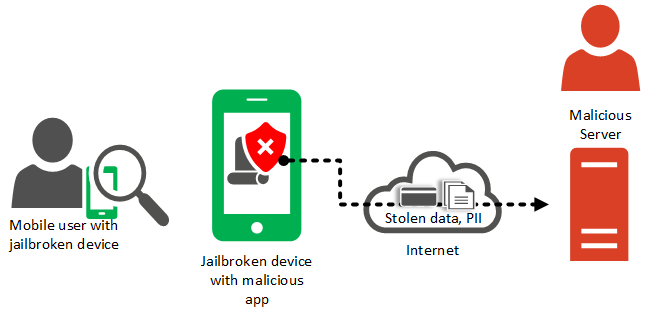
In scenario 2, the user owns a jailbroken device, which means that some applications are running with an extended level of permissions. The user has installed applications from unofficial repositories, one of them containing a malware.
The malware scans files on the device, looking for interesting data (PII, social security numbers, credentials) and targeting specific vulnerable applications that have not been patched.
The malware extracts data from the device and sends it to a malicious server.
Securing data
During the conception of a mobile app, one crucial thing is to clearly define what is stored in the application, why, and how.
Data stored on the device should be considered “unsafe” and only a strong requirement can justify that storage.
Development frameworks/APIs provide different technical ways to store data, that must be appropriately chosen depending on the nature of data you need to store.
If there is a clear need of storing data on the device, then evaluate the level of guarantee offered by the different techniques, and apply additional layer of encryption if needed.
Mobile devices (phones, tablets) must be considered as unsafe: they can disappear, they can be used by other people than their owners, and are privileged front-doors for cyber-attackers.
