
Multifactor authentication (MFA) is a central and widely used mechanism for strengthening the security of user accounts and access to a system.
Indeed, it is an authentication method that prevents many malicious attacks and exploits aimed at compromising data: brute force, session hijacking, privilege escalation, etc.
However, implementation and/or configuration errors very often make it easy to bypass this type of security process. Furthermore, users can be tricked through phishing or other social engineering techniques and thus allow attackers to bypass 2-factor authentication (2FA) or even multifactor authentication.
What is multi-factor authentication (MFA)? Beyond the principles and functioning of this type of process, this article will detail the common attacks and exploits as well as the essential best practices to strengthen the security of a multi-factor authentication.
What is multifactor authentication or MFA?
In most cases, authentication on a system (web or mobile application, infrastructure, network, etc.) is carried out through a user account (usually composed of a login and a password). This process makes it possible to prove the identity of a user and to assign him/her rights according to his/her role on the system (administrator for example).
To strengthen access control and account security, the process may require additional evidence, called factors, to confirm the identity of the same user: this is called multi-factor authentication. Increasingly used on many critical systems (SaaS applications, payment systems, etc.), an MFA consists of requiring users to use two or more factors during authentication. As the name suggests, a 2FA, which stands for Two Factor Authentication, will require exactly two factors of different types. And this is the mechanism most often implemented on most systems.
Furthermore, the term “strong authentication” is often used to refer to multifactor authentication. However, this is a misnomer. Strong authentication is based on a cryptographic protocol that must be resistant to certain types of attacks, whereas multifactor authentication only indicates that several categories of factors are used.
What are the main types of authentication factors?
Several types of factors can be used for multifactor authentication:
- A knowledge factor: password, confidential code, etc.
- A possession factor: smartphone, badge, USB key, etc.
- An inheritance factor: fingerprint, facial or voice recognition.
- A location factor: network connection, geographical position, etc.
More concretely, this can take the form of a push notification on the phone, a one-time code sent by SMS, a temporary rotating code provided by an application, a USB key, etc.
However, an MFA procedure has the disadvantage of adding friction for the user, with an extra step during authentication. In addition, the factors must be “available”, which is a difficulty that is sometimes underestimated in case of poor network coverage, change of phone or access during business trips for example.
Why implement multifactor authentication?
Between databases of credentials/passwords for sale on the dark web, brute force, social engineering, etc., attacks on authentication take many forms and are widespread. In most cases, attackers rely on data leaks to compromise systems, through credential stuffing for example.
To prevent these risks, the implementation of a multifactor authentication mechanism remains the ideal solution. Indeed, it is an indispensable measure to counter many attacks. However, it should not be seen as a guarantee of absolute protection, because, as with any mechanism, in the event of implementation or configuration errors, multifactor authentication can be bypassed. In addition, users can be tricked into unwittingly allowing attackers to bypass the MFA process.
What are the common attacks and exploits of multifactor authentication processes?
Several technical or human attacks and exploits can be used to bypass multifactor authentication. And to prevent these risks, security measures and tests are necessary. Let’s get to the heart of the matter with the most common attacks and exploits, as well as best practices to mitigate the risk of compromise.
Brute force of authentication factors
A common attack against multifactor authentication processes is brute force. For example, consider an authentication mechanism that uses a 4- or 6-digit code sent by SMS as a second factor.
In this case, an attacker would have to determine whether the target system has a limit on the number of attempts or a time limit after each failed connection. It should be noted in passing that the first mechanism can be easily abused, while the latter is much more effective.
Let’s go back to our example encountered during a web penetration test. The second factor consisted of a temporary 4-digit code (lasting 30 minutes) that was randomly generated. In addition, despite the rate limiting in place which blocked the IP after 3 failed connections, it was possible to use different tools to change our IP and continue our brute force to guess the second authentication factor within the time limit (30 minutes).
Thus, it was possible to bypass this 2-factor authentication and access a user account on the target platform. This exploitation was possible for two reasons:
- A 4-digit code, even if randomly generated, can be guessed with the right tools, and much more easily if there is no time constraint. Indeed, it is necessary to generate a sufficiently long and random code, with a reasonable lifetime.
- Implementing a limit on connection attempts and rate limiting (with IP blocking) is essential. However, implementing a timeout after each connection failure might have been the blocking mechanism to crack the second factor code.
For more information, you can read our dedicated article : Brute force attacks: principles and security best practices.
Session hijacking and account theft
To reduce the friction of multifactor authentication, many web applications include a “Remember” feature. This functionality is usually implemented through a cookie or a session token.
When we encounter this case, we observe whether the cookie is incremental or follows a logical construction that would allow us to guess or create it. In addition, the cookie must have the httpOnly attribute to complexify the exploitation of XSS vulnerabilities.
In addition, the password reset procedure is a critical aspect that must be well implemented and tested. Indeed, it may happen that some procedures directly reconnect a user following the creation of a new password, and this without asking for the second factor initially activated to confirm his identity.
Similarly, it is sometimes possible to disable multifactor authentication without knowing the second factor because the system simply does not ask for it.
Manipulation of requests and responses
By intercepting traffic to analyse the operation of an authentication system, it is possible to perform various tests.
Firstly, it is a matter of testing the change in the status code of a response. For example, from success=false to success=true or HTTP/1.1 422 Unprocessable Entity to HTTP/1.1 200 OK. In some cases, it may be possible to bypass authentication using this method.
Sometimes the authentication process may check only the validity of the second factor, and return the result of this check in the request. In this case, it might be possible to modify the content of the response with the correct parameter to access an account. Indeed, during tests we encountered a case where a 2FA parameter could be removed from the request, which allowed us to authenticate.
Social engineering attacks
To bypass multifactor authentication processes, attackers rely heavily on numerous social engineering techniques. Indeed, even the most secure system is outdated if users are not aware of the risks of phishing, vishing, etc.
Phishing associated with AitM or Adversary In the Middle
Adversary in the middle (abbreviated to AiTM) is a technique that consists of sending a phishing email containing a link to an interface clone.
The attacker’s objective is to position himself between a user and a legitimate site to intercept the traffic with the help of a proxy. When clicked, the user will be redirected to a clone page of the legitimate site, let’s say an authentication page with multiple factors in place.
The cloned site will display the same interfaces during the various stages of MFA authentication and the user will provide his/her correct information. The objective is to retrieve the session cookie passed after successful authentication and use it to log in.
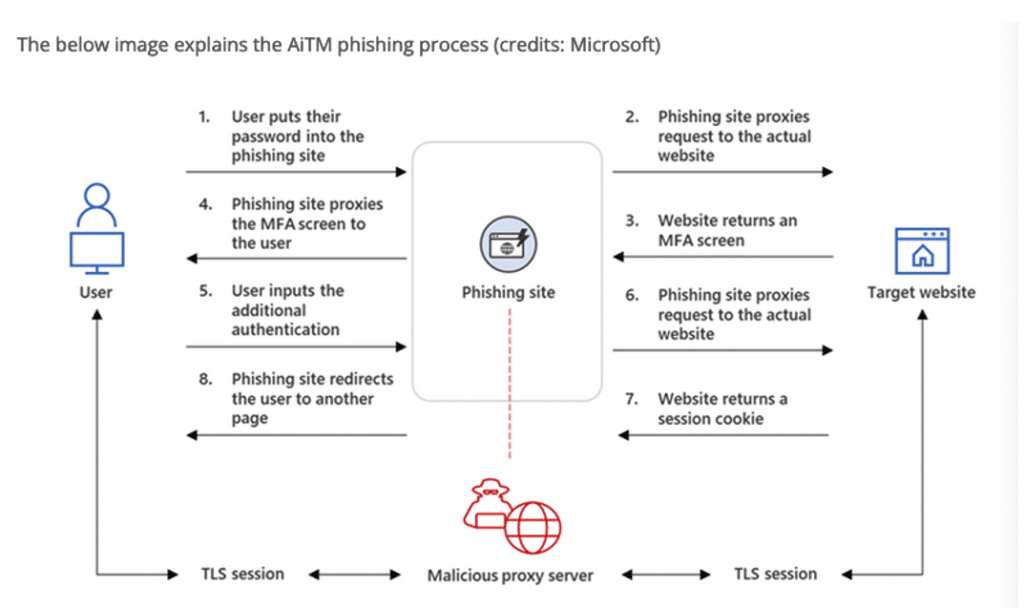
This attack technique can work for all types of multifactor authentication. It is very easy to implement, as there are frameworks that make it easy to set up the proxy.
To protect against this, user awareness is crucial. A social engineering pentest can serve this purpose. In addition, it may be worth considering conditional access rules (location criteria, authorised device, etc.) or switching to authentication with a physical factor (a USB key, for example), for very critical systems, as an attacker will not be able to recover it remotely.
Voice phishing (vishing) attacks
Vishing is a variant of phishing. It involves an attacker calling a target with the aim of getting them to perform an action: disclose sensitive information, click on a link, download an attachment, etc.
To achieve this, the attacker will create a “believable” story, which will be even more believable if he/she manages to spoof a phone number.
For example, let’s take a vishing scenario that we carried out to bypass multifactor authentication during a pentest:
- In the context of black box testing (without prior information), after a recon and the identification of target profiles on LinkedIn, we called some contacts.
- The pretext: being from the IT department, we had to “urgently” update the VPN used in the company, due to a security flaw that “could cause damage” if not done quickly.
- The request (somewhat formalised in the form of an injunction) was as follows: we needed “quickly” the password and the second factor of “each member of the team” (in this case a code sent by SMS) in order to carry out this update and thus guarantee the security of each workstation.
- Although the request may (and should) appear “lunar” to technical profiles or individuals aware of social engineering attacks, we used malice to achieve our ends. Indeed, we managed to get what we wanted by relying on natural human psychological springs (urgency, feeling of belonging to a group, desire to help, fear, etc.), by targeting non-technical profiles (in key positions) and those who are less aware of the risks in appearance (and in reality).
MFA Push bombing or Push spam attacks
To bypass 2FA authentication, an attacker can spam the target with push notifications.
This is the method that allowed attackers to compromise Cisco, Twilio and Uber between May and August 2022. As detailed in the Cisco or Twilio incident reports, the attackers first obtained the credentials of a target’s email account. They then managed to bypass the multifactor authentication by spamming the target with numerous phishing solicitations until the target validated the notification.
This technique takes advantage of Push Fatigue or Push spam. Indeed, as the notifications are very frequent, they create a lassitude in the targeted person and thus a decrease in attention.
