After a security audit, you have been notified flaws. Critical, important, medium: do you know how this is assessed? We describe here our methodology, based on the OWASP* one, to estimate the severity of the risks associated with the vulnerability.
What Is the Criticality Level of a Security Flaw?
Technical or logic flaws are assessed according to their severity and potential consequences. Clear and precise criteria -described below- allow us to estimate objectively the severity of vulnerabilities. Transparency in the criteria and in the assessment increase trust between security, development and managerial teams. This helps also to prioritise corrections.
In practice, a level of criticality is attributed to each vulnerability detected: low, medium, high or critical. The level of criticality incorporates the likelihood of a vulnerability to be exploited and the potential impact. Once these two elements are rated with a score, the final criticality will be set up.
Likelihood of Exploitation of a Security Flaw
It represents the possibilities that the flaw is indeed found and “used”. The exploitation of the flaw can be voluntary (attack of a malicious person) or not (incidents related to a particular use of the platform, by a person or an automated tool).
The first step is then to evaluate this actor, the potential attacker:
- What are his competencies?
- What are his motivations – meaning, the expected reward -?
- Does he have, or can he have the necessary resources? (user account, specific privileges, financial input…)
- How is he linked with his target? (anonymous outsider attacker, authenticated user, intranet attacker, partner…)
Then the vulnerability itself has to be considered:
- Is it easy to discover and to exploit?
- Is it a known or unknown vulnerability?
- Which mechanisms are there to potentially identify the attacker?
Potential Impact of a Security Flaw
It is also formed of two elements: the technical impact and the business impact.
The technical impact is to be measured for the loss of data confidentiality and integrity, the loss of availability of services and if the attack is traceable (an undetected attack will have a stronger impact on the long-term).
The business impact takes into account the financial damage of the attack, the reputation damage to the business, its responsibility in front of the law and the scale of privacy violation of its users (one individual? a group? a million people?)
Assess the Global Criticality of the Vulnerability
For each criterion mentioned, we give a score between 1 and 9. Scores match a verbal appreciation in order to guide and homogenise the representation of these numbers.
In the rating of the impact for example, we can have the criterion loss of integrity of the data, with:
1- No corrupt data
2- Minimal slightly corrupt data
3- Minimal seriously corrupt data
4- Minimal totally corrupt data
5- Extensive slightly corrupt data
6- Extensive seriously corrupt data
7- Extensive totally corrupt data
8- All data potentially corrupt
9- All data totally corrupt
To rate criteria relevantly, you need to set it in a coherent attack scenario with the situation. As often in risk assessment, we will choose the worst-case credible scenario.
Let us take an e-commerce website of a major group with a vulnerability in the shopping cart (possibility to change the amount of the shopping cart before ordering). An exploit scenario could be “a group of receivers place a massive order for a ridiculously low price in order to sell them on the black market”. If the website is specialised in clothing, furniture or even cycles, this is a coherent potential scenario. However, if the website is specialised in pet toys, it is more probable than an individual place a personal order with price modification (depending on the technical knowledge needed to find and exploit the vulnerability).
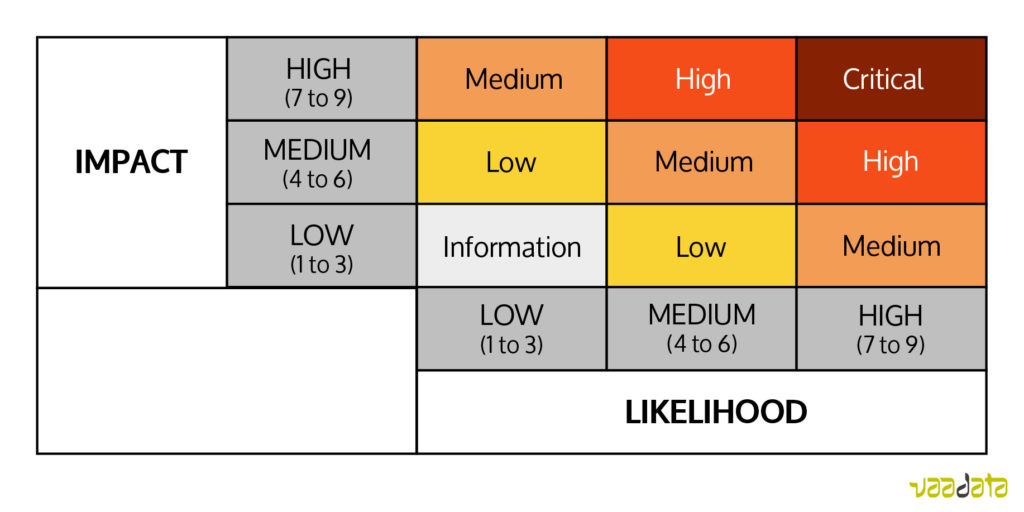
Once all the factors estimated, we calculate the average for the likelihood of exploitation as well as for the potential impact. We can then determine the global criticality by multiplying the two numbers found, or by looking at the under table:
If the rating (average of grades) for the likelihood of exploitation is 4 (Medium) and the rating for the potential impact is 8 (high), then the vulnerability criticality is HIGH.
To conclude, risk assessment of vulnerabilities is based on clear and understandable criteria. Each company context and stakes are decisive for the global risk estimation, and for then setting correction priorities of the vulnerabilities.
On the whole, as the OWASP says here, “if discovering vulnerabilities is important, being able to estimate the associated risk is just as important”.
OWASP*: The Open Web Application Security Project (OWASP) is a worldwide not-for-profit charitable organization focused on improving the security of software. OWASP is in a unique position to provide impartial, practical information about AppSec to individuals, corporations, universities, government agencies and other organizations worldwide.