Burp is an essential offensive security tool. It is used by a majority of professionals (including us pentesters) and is dedicated mainly to pentesting web applications.
In this article, we’ll take a look at Burp Suite’s main features and key extensions.
What is Burp Suite?
Burp Suite is a software package dedicated to web security audits (web penetration tests). It has been developed by PortSwigger, a leading company in the world of web security.
Burp Suite, often referred to simply as Burp, is optimised and designed to meet the needs of professional pentesters, and is the most widely used tool in its field. It is a modular tool that allows both manual and automated tests to be carried out, helping pentesters to effectively identify vulnerabilities in web applications.
Different versions: Burp Suite Community and Professional
Before going any further, it is important to note that Burp Suite is available in two different versions:
- Burp Suite Community Edition
- Burp Suite Professional
The first is free, but has fewer and more limited features than the paid “Professional” version.
As its name suggests, the Professional version is designed for professional use, and is the basis for this article.
What are the advantages of Burp Suite?
During a web penetration test, a pentester will generally use Burp Suite 90% of the time, which makes it an essential tool. There are alternatives such as ZAP, developed by OWASP, but Burp Suite remains the benchmark in the world of web pentesting.
Burp’s overall operation is modular. Some of its modules are installed by default on the software. These are the essential modules for conducting an audit. Other complementary modules called extensions are available for download via the extender (Burp’s ‘catalogue’).
Burp Suite’s strength, apart from its modularity and user-friendliness, lies in its very active community, which develops new extensions and creates detailed documentation on the modules.
Burp is a comprehensive tool that will meet most of a pentester’s needs. Even if the basic functionalities do not meet a specific need, in most cases there is an extension developed by the community for this purpose.
Exploring Burp Suite’s Features
Interception Proxy
Burp Suite’s main feature is the Proxy. The Proxy enables Burp to act as an intermediary between the client (web browser) and the server hosting the web application.
By placing itself between these two components, Burp will be able to intercept all exchanges and requests made between the web browser and the server. The pentester will therefore be able to analyse the requests in detail and, if it wishes, modify them.
To modify requests, the Proxy intercepts requests one by one and lets the pentester choose whether to let them through or reject them. If it lets them through, it can modify them before transmitting them to the server.
The Proxy also allows the history of requests to be viewed live without having to transmit them manually to the server. In fact, this is the Proxy’s most frequently used mode.
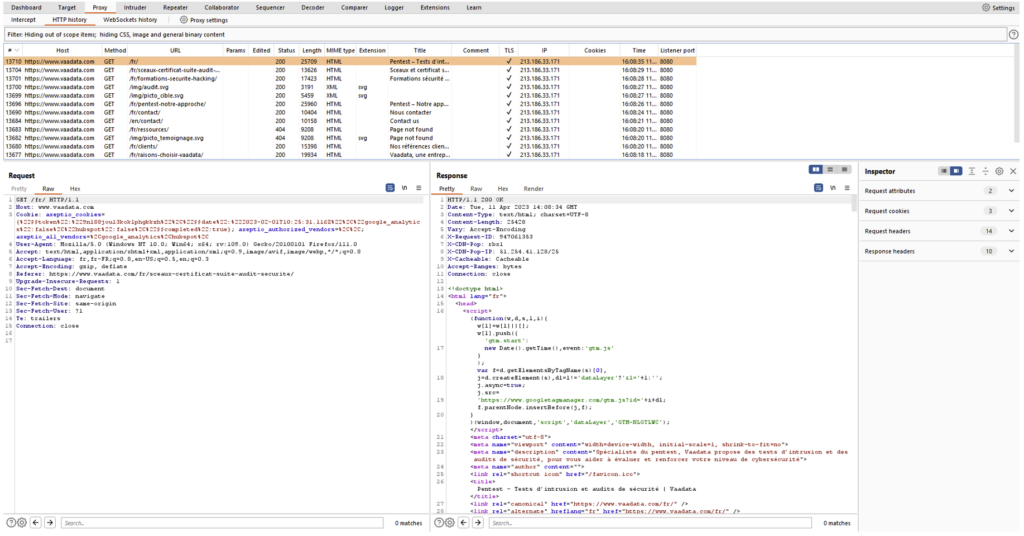
The image above shows the history of requests made to the “vaadata.com” domain. When a request is selected, it is possible to see the request sent by the browser and the response from the server. Each time the pentester interacts with the web application on its browser, a new request will appear in the history.
Burp Repeater
The Repeater is the module that allows requests to be replayed at will. As its name suggests, the pentester will be able to repeat requests and modify them as it sees fit before sending them to the server.
It can then analyse the server’s response according to what it has modified. The Repeater is often used to manually identify and exploit vulnerabilities.
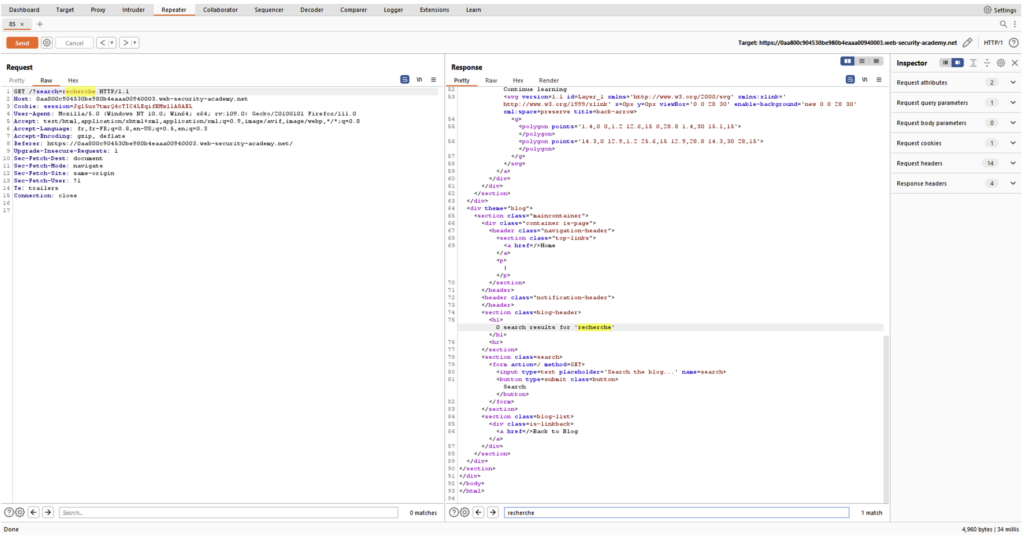
In the image above, we can see that the basic request is made up of a URL which takes the word “search” as the parameter “search”.
Thanks to the Repeater, the pentester can replay the request and test, for example, whether JavaScript code injection is possible:
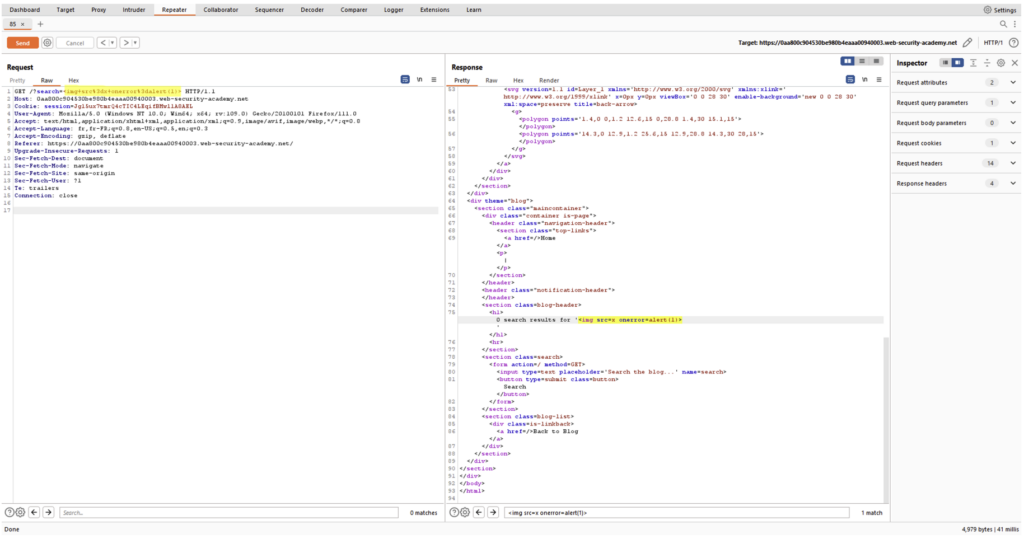
In this case, the Repeater helped identify an XSS vulnerability.
Burp Intruder
The Intruder is a powerful tool that can be used to automate the sending of a request containing a customised payload. For example, the Intruder can be used to automatically increment a value and send each increment to the server. The Intruder will enable the pentester to automate tedious tasks that are impossible to carry out manually, such as sending several thousand requests. The possibilities for using the Intruder are virtually infinite, allowing several payloads of the same or different types to be added.
The Intruder has a “Positions” tab where the pentester can define the position of the payload in the request. He can then choose the type of payload to inject in the “Payloads” tab.
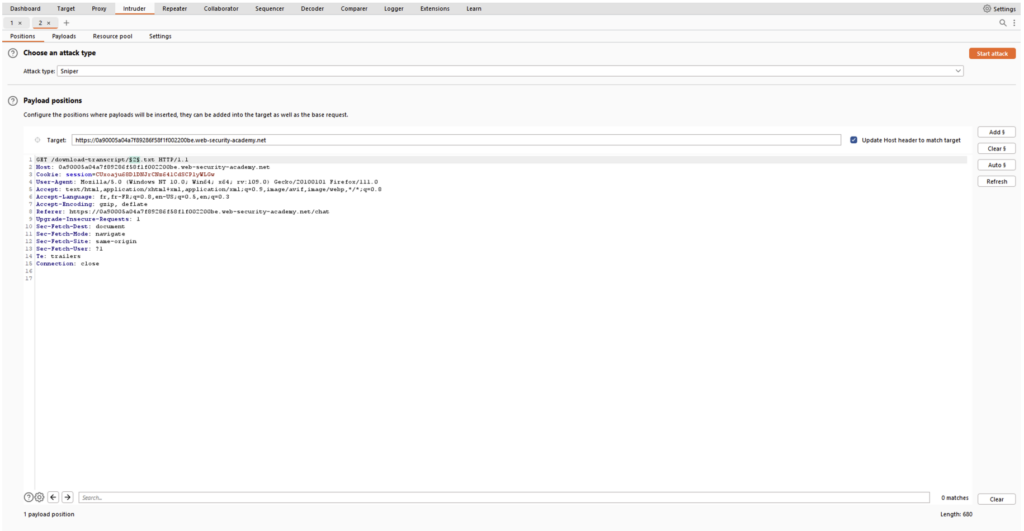
In the image above, the basic query calls up a “2.txt” file. Using the Intruder, you can test whether files 1 to 100 exist, for example. To do this, simply place the “§” signs around the value we are going to increment and choose a range from 1 to 100 in the “Payloads” tab:
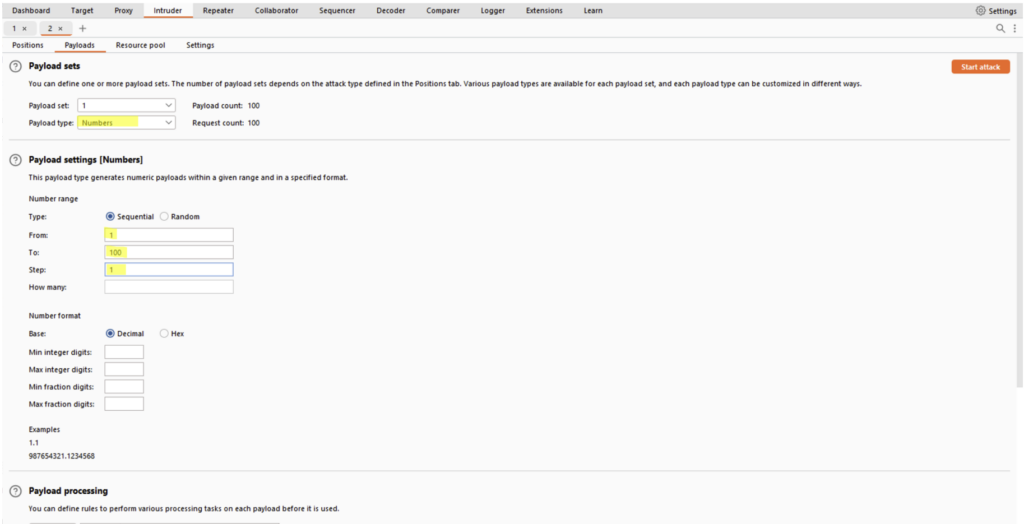
Then simply press the “Start attack” button to launch the Intruder with our configuration. A window will appear showing the results of the various requests:
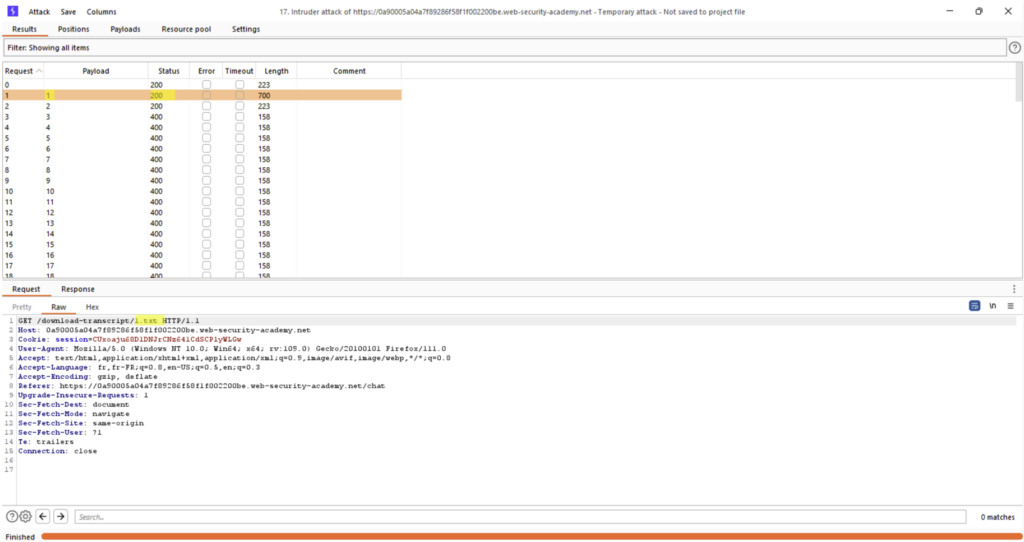
In this case, we can see that the “1.txt” file also exists.
The Vulnerability Scanner
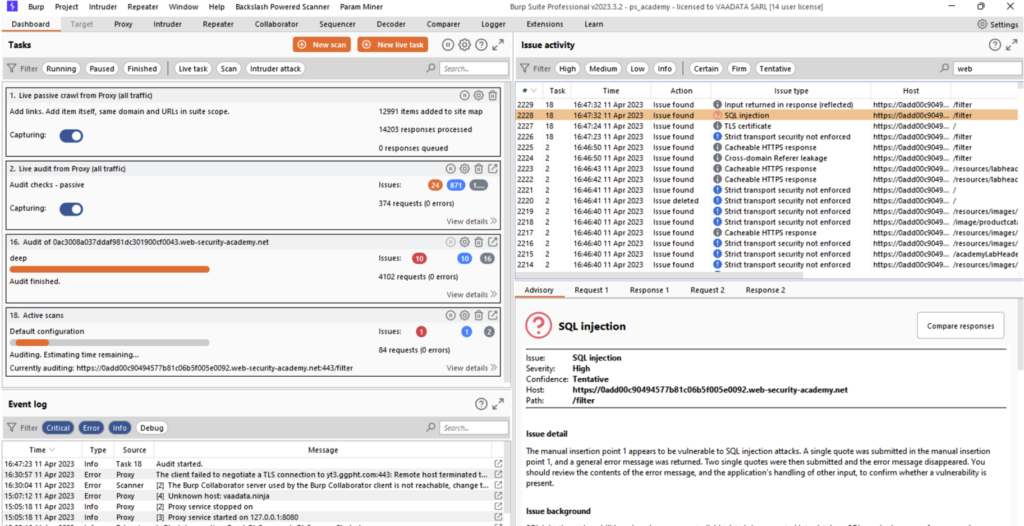
The Scanner is one of the most useful features of Burp Suite’s Professional edition. The Scanner automatically performs passive scans on all requests between the client and the server, and active scans on requests selected by the pentester.
A passive scan is a type of scan where the traffic is analysed and vulnerabilities are identified if patterns are recognised by the scanner. For example, Burp’s scanner will report information if it detects email addresses in server responses. During passive scans, the scanner will not modify the requests.
Conversely, an active scan is a type of scan where the scanner deliberately modifies the request. The scanner injects malicious payloads into one or more requests chosen by the pentester and analyses the server response. If the scanner identifies a patern that is the direct consequence of the injected payload, it will report a more or less critical vulnerability.
Burp’s Vulnerability Scanner is therefore an essential tool for the pentester, saving time and improving efficiency.
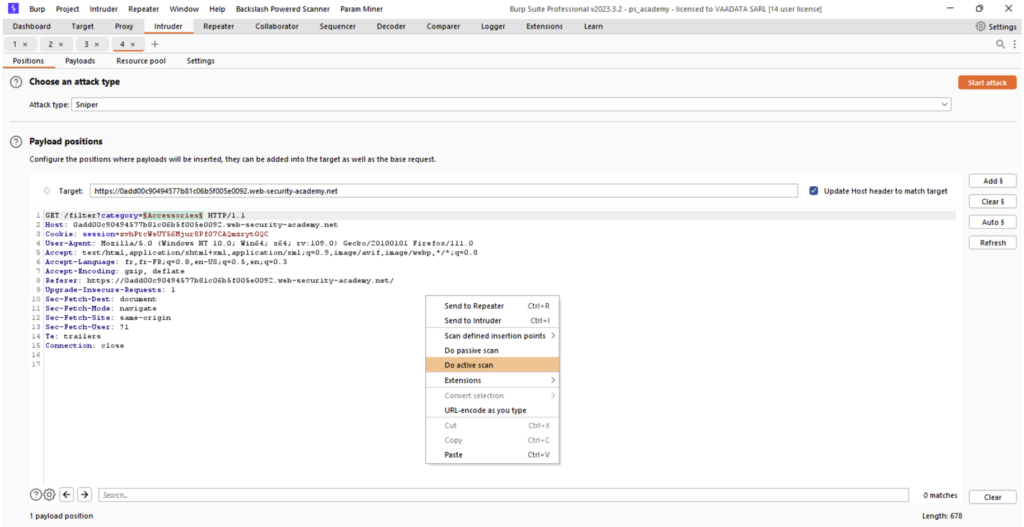
To launch an active scan, simply send the request to the Intruder, specify the payload position in the same way as for traditional Intruder use, right-click on the request and press “Do active scan”.
The result of the scan will then be visible in Burp Suite’s Dashboard tab:
Burp Collaborator
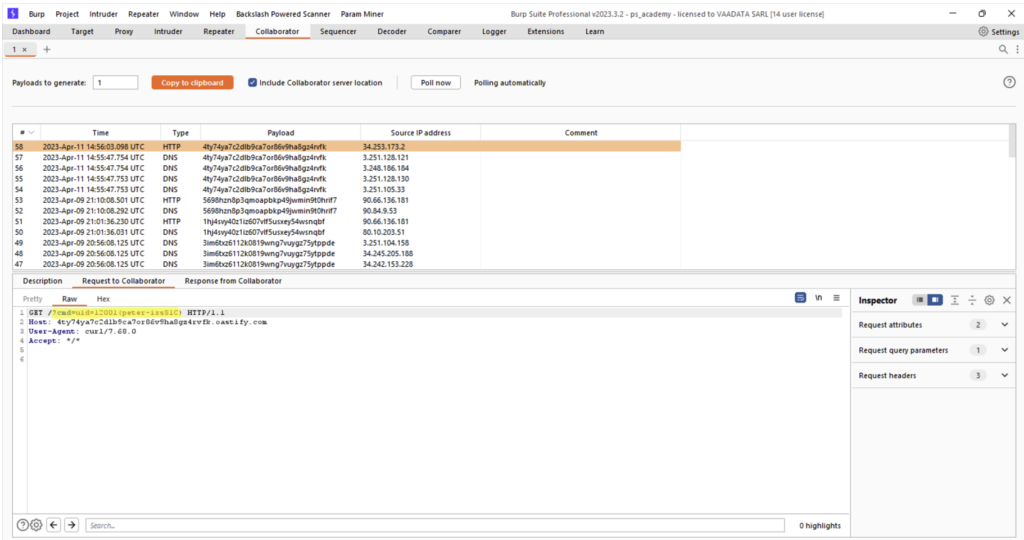
Burp Collaborator will enable the pentester to have a third-party platform on the Internet, accessible from anywhere. The Collaborator will be used in particular to exploit vulnerabilities that do not return any information in the server response enabling the vulnerability to be validated.
We’re talking about vulnerabilities that return no errors, no abnormal responses or that cause no delays.
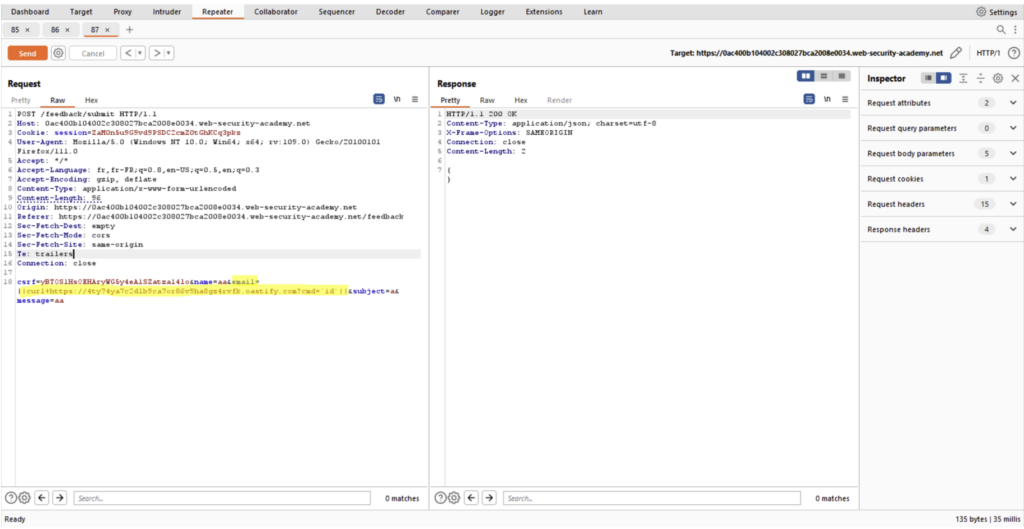
For example, if the vulnerability in question allows system commands to be executed on the server but the result of the command cannot be viewed in the server response, the Collaborator can be used to exfiltrate the result of the command.
In the following example, we can inject a system command into the “email” parameter, which will execute a “curl” on the Collaborator url and retrieve the result of the command using the Collaborator:
The Top 7 Burp Suite Extensions
Extensions are the essence of Burp’s community spirit. It is possible to add extensions developed both by PortSwigger and by the community to meet additional needs and extend Burp’s capabilities.
As its name suggests, Burp’s Extensions section lets you download official or community extensions. In the rest of this article, we’ll look at the extensions we consider essential for a web pentester.
Active Scan ++ and Backslash Powered Scanner
These two extensions are very useful for extending the list of tests performed by the Burp Scanner. Thanks to these two extensions, the pentester can potentially identify vulnerabilities that would not have been detected by the basic scanner.
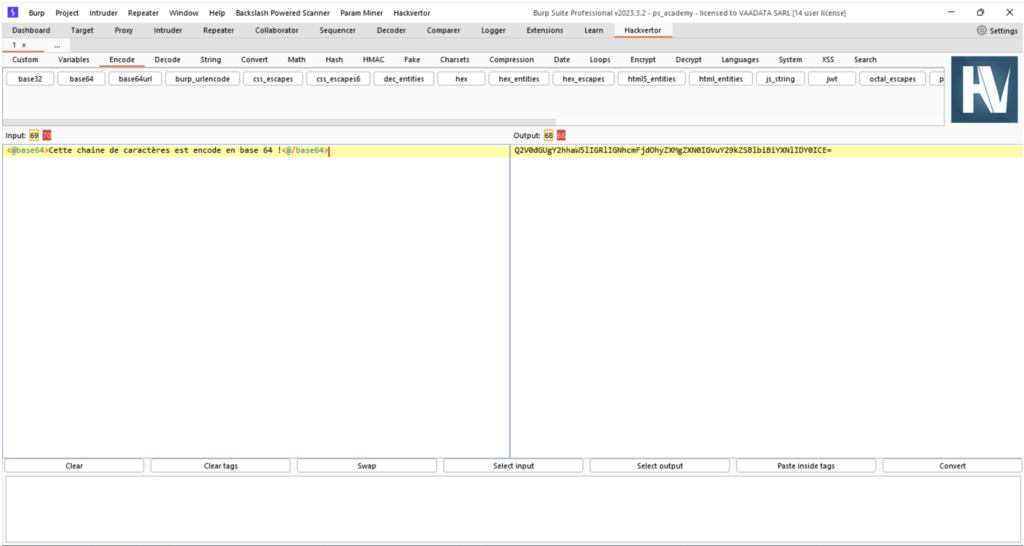
Hackvertor
Hackvertor is a toolbox for converting any character string into the desired encoding. This extension uses XML tags around the character string to specify the type of encoding or conversion to be used. It is also possible to use these tags in any Burp module such as the Repeater or Intruder, and it is also possible to create your own XML conversion tags for advanced use.
Auth Analyzer and AuthMatrix
These two extensions will make it easier for the pentester to test rights. For each request, Auth Analyzer or AuthMatrix will replay the request with different rights configured by the pentester.
For more details on how AuthMatrix works, see our article: Burp features and extensions to gain efficiency.
As regards the difference between these two extensions, AuthMatrix is more commonly used when the pentester has a small number of requests to test or if certain requests perform sensitive operations that should not be repeated, such as creating or deleting data. The pentester must select the requests to be tested.
The Auth Analyzer extension is simpler to use and is often used when a large number of queries need to be tested. Queries will be automatically replayed with different rights as the pentester moves through the web application.
Param Miner
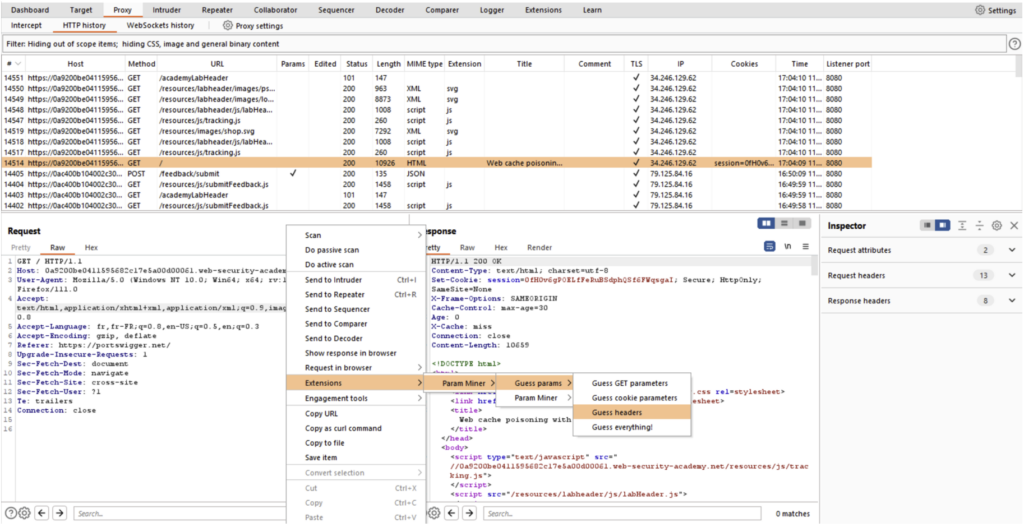
The Param Miner extension can be used to search for hidden headers or parameters in a given request. This extension is particularly useful for identifying “web cache poisoning” type vulnerabilities.
To use it, simply right-click on the query you want, select ‘Extensions’, ‘Param Miner’ and choose the type of test you want to run. In the example below, we’re trying to find hidden headers:
If a header is found, a vulnerability will be reported in the “Dashboard” tab:
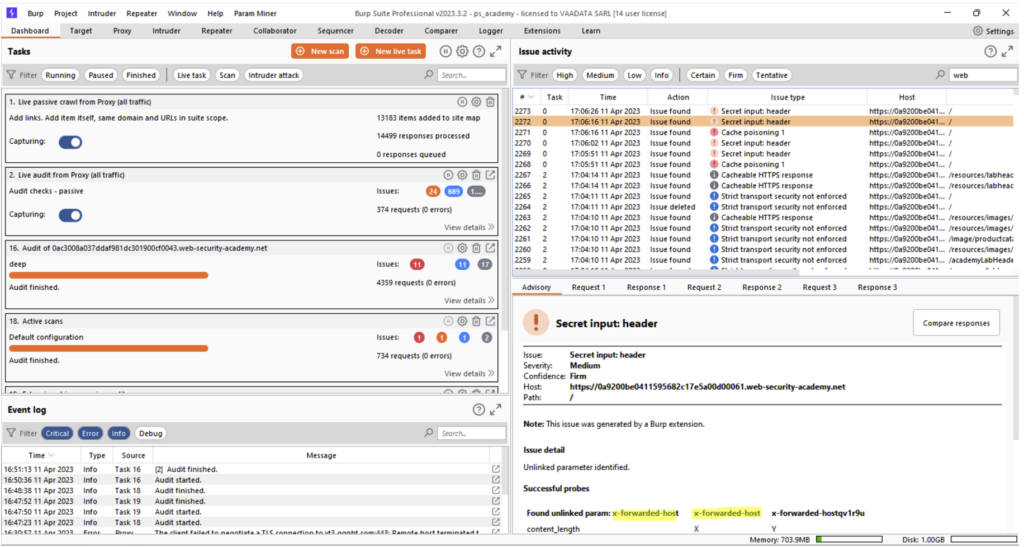
In our case, Param Miner identified that it was possible to use the “X-Forwarded-Host” header.
Stepper
Finally, Stepper is an extension that lets you replay a sequence of selected queries. Stepper can also be used to define dynamic variables in the sequences, which can then be reused in certain Burp Suite modules such as the Repeater or the Intruder.
For more information on this extension, you can read our article: Auditing an application protected by a CSRF token with Stepper.
Author: Lorenzo CARTE – Pentester @Vaadata
