Phishing evolved a lot. Whereas fraudulent email was before easily detected by its obvious spelling mistakes and its exaggerated request or threats (immediate bank transfer, account completely deleted…), it uses nowadays codes of trusted institutions. Phishing email involves besides personalized demand or known contacts of the attacked person (a manager for example), which makes it hard to detect.
Phishing aims an interaction with a tricked email. It is the most used method in social engineering, a branch of cybercrime.
Social engineering targets human behaviour. Its purpose is to lead a user to reveal confidential information and to realise harmful actions for themselves or for an organisation the user belongs to. You can raise awareness of your team about this risk by conducting a social engineering audit.
We will see in this article how to avoid different phishing strategies, which can be tricky even for experienced and attentive users.
How to Detect a Malicious Email?
1. Subject and content
You should be careful to subject lines that are driving you to click: showy news, special offers, invitations to gain this or that, urgent help needed, or even problem on your bank account
If they are not bad promotion or newsletter, it is very likely they are an attempt to make you click.
More than the subject line, the body email will reveal you the questionable intentions of the author. Without taking into account the author (we will analyse the source of the email later in the article), some content has to raise your awareness. We mean, the content asking personal or confidential information and/or documents, or asking (explicitly or not) to realise specific and often unusual actions as:
- Proceeding to a financial transaction
- Giving your user identification, including password
- Sending an official document (ID card, payslip…)
- Opening an attached file
- Following a link
- Realising an action after the link (log in, filling up a form, downloading a document…)
Excuses can be numerous and some seem legitimate enough to do the action without wondering. Some pretenses can as well play with sentiments and emotions in order to trick reason. You can check our article giving some psychological drivers used to push people to click.
Be particularly careful to following categories of excuses
- Technic and security (“Update your password here” – “Following an update, please log in here to confirm your account” – “Following a cyberattack, check if your password wasn’t stolen by signing in here” – “Your account will be suspended for inactivity. To keep your account, log in here…”)
- Alluring and commercial (“Win a free smartphone by filling out our form” – “The incredible discovery of a whale who was teaching mathematics at Paris University. Install our app to read the article” – “Special offer for the first new registered members”)
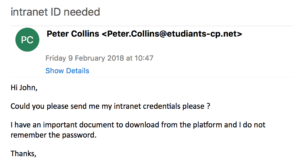
- Unusual procedure (“Can you please send my pay slip per email, my intranet is not working” – “I need you to pay this invoice quickly, Mr Doe is unavailable and can’t do it”…)
2. Check the source
2.1. Unknown
If you do not know the sender, you need to verify its identity: does the person / the company exist?
A quick research with search engines reveals generally fake sender. For companies, check for example its online presence (website, external reviews…)
For more specific situations, ask confirmation to an appropriate person. Take the case you receive an email from a person who introduced itself as “the new intern”. This person asks you for confidential information. Seek confirmation of its existence from your human resources department.
2.2. Identity fraud: close email or domain
If the sender pretends to be a person that you know or belonging to a group that you know, you need to verify this identity is not stolen. A simple usurpation consists in using a close email address to the real one of the person the attacker pretends to be.
You receive for example an email from your colleague Peter asking if you could give him again the password for the intranet account that you created for him two months ago.
Careful, you observe the email address of the sender. You know his real address is: [email protected]
Here are some examples that you may encounter:
- Character change: Peter.Coli[email protected], Peter–[email protected]
- Character inversion: Peter.Colil[email protected], Petre[email protected]
- Using of a close domain: Peter.Collins@etudiant-cp.net, Peter.Collins@etudiants-cp.ne, Peter.Collins@etudlants-cp.net
Possibilities are numerous, and even though they are here quite evident to see, it can be difficult to notice this kind of modification. Especially as with a lack of attention, the email address may not even be read by the targeted person.
If in doubt, do not hesitate to contact the person to confirm its identity:
- Send a new email (it is better not to answer the suspicious email)
- Call the person
- Meet the person
2.3. Advanced usurpation
It exists a more transparent method to usurp an email address, almost undetectable for a user without advanced knowledge. The usurper will indeed show the exact sending address as the one usurped.
It seems a perfect trick? Don’t worry, it is still possible to detect this attack.
In cases the usurper is waiting an email answer, you can detect the misuse when clicking on “Reply”. To continue the example from above, the impostor could indeed send an email showing [email protected] as email address (identical to the authentic address).
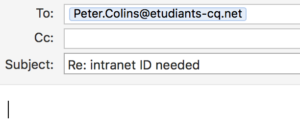
But, as the attacker does not own properly this address, he will not be able to receive the answer if it is sent to that address. Once clicking on “Reply” you may discover the fake address as the ones detailed above.
In other cases, the attacker might not want an answer (in case he is asking you to realise an action as downloading or executing a malicious file).
It is then harder to detect the deception.
All users should be attentive to the email content. Being careful makes possible to arise suspicion, which will be confirmed by contacting the potentially usurped person (with a call, a new email or a meeting).
An advanced user can, moreover, have a look in the headers or verify if the sender IP address is corresponding to the expected one of the mail server.
3. Attached file (malware, zips…)
In main cases, attached files are automatically scanned and screened in order to prevent any potentially malicious file to reach your mail box. However, there are other approaches to bypass this protection, like creating an encrypted archive (requiring a password). The attacker can give fake excuses for this, as “file needed compression as it is too big” or the wish “to make file confidential” (security argument).
In those conditions, files can hide every sort of malicious code, and it is then recommended neither to download nor to open attached files. If files would be legitimate, there is no reason not to send them by the usual procedure (unusual methods should alert). Classic files as PDF and Word (.doc and .ppt) can in theory not transport malicious code, that’s why they are transferred by email. Note though that attached file is never 100 % guarantee without malware, as the recent vulnerabilities discovered in file .docx show.
More generally, when opening a file, a window can open and ask you if you want to execute the program. An execute program is potentially very dangerous, and it is very unlikely that you receive legitimately that kind of file per email. We can actually mention that the two main extensions used for phishing attacks are .exe and .hta. Do not execute those file.
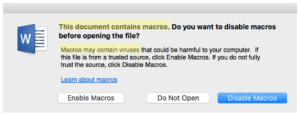
Last but not least, a specific Word file can also have macros (.docm). When opening this file, it will ask you if you want to activate macros. Macros are potentially dangerous. They are used only in specific cases (complex professional documents) ; therefore there is no reason -in most cases- to active them in a classic file. Refuse to enable macros, and make a habit of even not opening those files (.docm).
4. Links
4.1. Verify domain and URL
When a link is available in an email, it is important to check the destination of it (before clicking on it preferably). A simple way consists in passing your mouse pointer on it and it will show the destination. You should indeed never trust the shown URL as it is only a visual one and gives no information regarding the real destination.
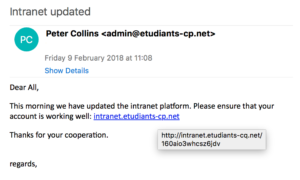
Once the real destination shown, read carefully the access path (and especially the domain name) to detect usurpations. In the example below, a close reading allows to detect the attempted fraud: the destination website is intranet.etudiants-cq.net and not intranet.etudiants-cp.net. This website can then be hold by an attacker and meant to mislead users.
If a website seems suspicious, prefer to access it from a research engine rather than following the link.
4.2. Behaviour
When a link is sent per email and seems legitimate, you will certainly click on it. If reading the email did not arise suspicion, some behaviour of the application should alert you:
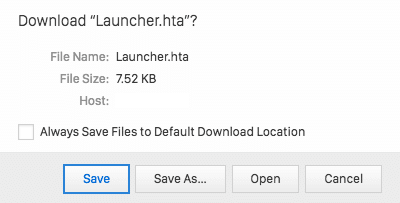
- Downloading a file: If a file is downloaded in your browser whereas you expected only to land on an internet page, it is highly possible that you are not on the website you thought to be. Verify the URL and do not download the file. Prefer to receive attached files (generally verified by an antivirus).
- Login form: avoid entering your user login after following a link. Legitimate cases when you will be asked to reconnect are rare, whereas attempts to steal passwords this way are many. If you need to log in again, prefer to access the needed website without following the link of the email, rather by a search engine for example.
In conclusion, as we saw in this article, many methods can be used to mislead a web user and prompt this user to do a sensible action. We can all, at one point or the other, fall into the trap. Not rushing when opening emails and checking all elements before mentioned will protect you from phishing.
Phishing is the most used method in social engineering. We do conduct social engineering penetration test since several years. Our clients shared their experience feedback and what they learned from it.