Do you know why phishing is so dangerous?
Because it combines IT skills with knowledge of human psychology. In fact, a phishing email relies on human psychological drivers to first get the opening of the email and to then push to click.
Technical skills are of course necessary to increase the likelihood of clicks, e.g. to spoof a legitimate sender, to create an interface clone, to forward to malicious domains, etc.
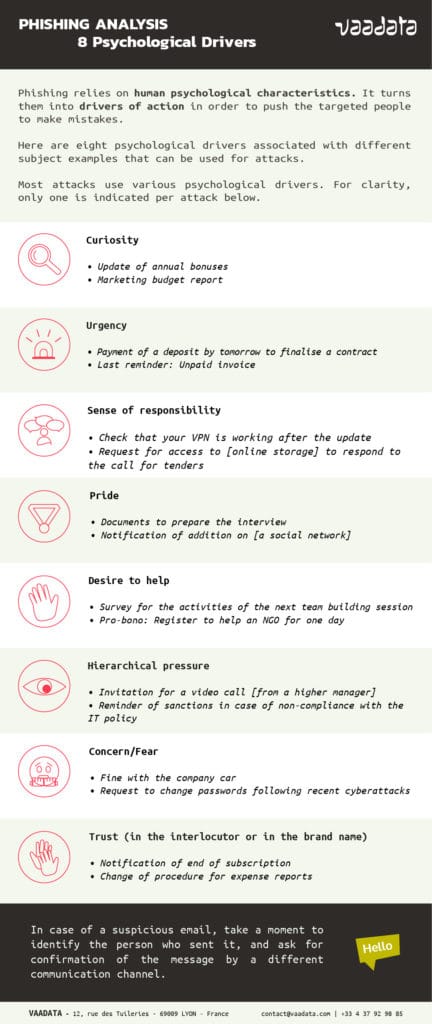
But today, we will look into the psychological drivers that drive action during phishing. We have taken 8 commonly used drivers and associated them with different subjects that can be used as pretexts for phishing.
Most attacks use various psychological drivers. For example, if we take the third pretext: “Payment of a deposit before tomorrow to finalise a contract”, there are many psychological drivers that can be used by attackers to persuade the targets to click:
- Urgency, with the “before tomorrow”
- Sense of responsibility: you are probably the person in charge of transactions if this email is sent to you, paying a deposit would be part of your duties.
- Desire to help: the “to finalise a contract” appeals to your desire to help. If you want your company/co-worker to succeed, when you have the opportunity to do something to help, you will do it.
- Trust in the interlocutor: it is probably a colleague you know who is asking for this transfer.
- Etc.
For clarity reasons in the infographic, only one is indicated per attack below.
Many psychological drivers can be used to manipulate a targeted person. We can all, at one time or another, fall into one of these traps.
The first step in protecting yourself is to become aware of the “strings” that attackers use to push to action and then to acquire the keys to identifying suspicious emails.
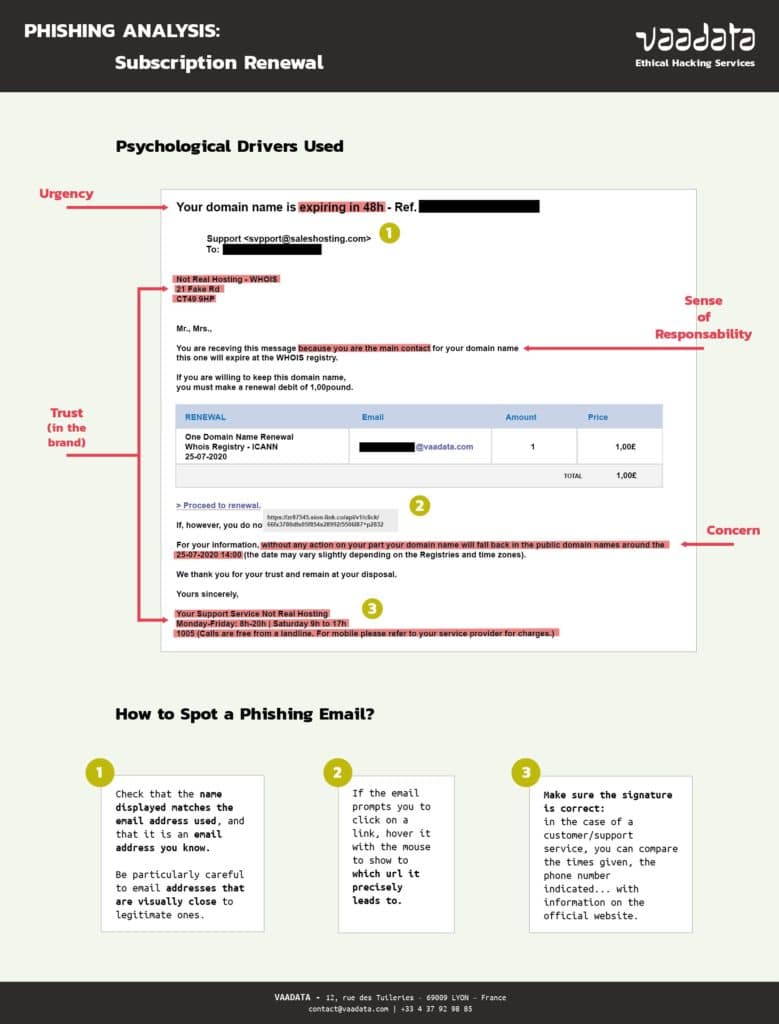
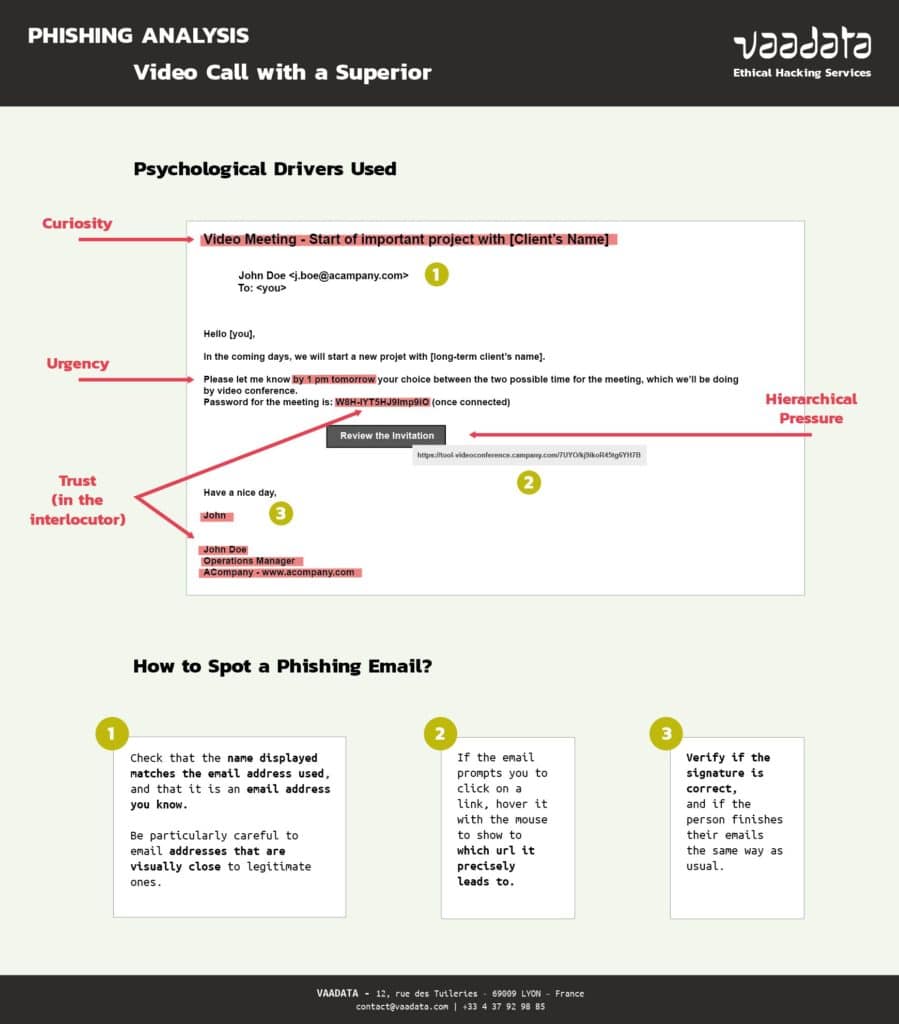
Here are some phishing examples, highlighting the mental drivers used. We have also taken from the article mentioned above three elements to verify in order to spot if it is a phishing email or not.
Finally, a social engineering pentest can be carried out to raise awareness of this type of attack among company employees through realistic scenarios that will be remembered.