

Like other cloud services, Azure is a prime target for attackers. This is due to its growing popularity and strategic importance for businesses.
To reduce the risk of security breaches, it is essential to implement robust security measures. It is also important to understand the types of attack and assess their potential impact.
Man in the Middle (MitM) attacks exploit network configuration flaws and the absence of robust security mechanisms to guarantee the integrity and confidentiality of exchanged data.
These attacks consist of intercepting and manipulating communications between two parties, generally a client and a server, without their knowledge.
With a good Internet connection and high-performance hardware, users can have the impression that their actions on a web page are instantaneous or almost.
However, it should not be forgotten that a server takes time to process requests. Even if it is a matter of milliseconds, this delay may be of interest to an attacker. These are known as race condition attacks.
Various subdomain enumeration techniques are used to identify the attack surface of a domain or organisation.
The aim is to obtain as complete a list as possible of all the subdomains associated with the targeted domain.
At Vaadata, we carry out this type of enumeration almost systematically during our audits. This is done as part of a global reconnaissance phase, in order to provide our clients with an overview of the subdomains and servers exposed.
Kerberos is an authentication protocol used in a Microsoft Active Directory context. The lack of knowledge about how it works can lead to the introduction of vulnerabilities that can be exploited by an attacker.
In this article, we will explain the principle and operation of the Kerberos authentication protocol.
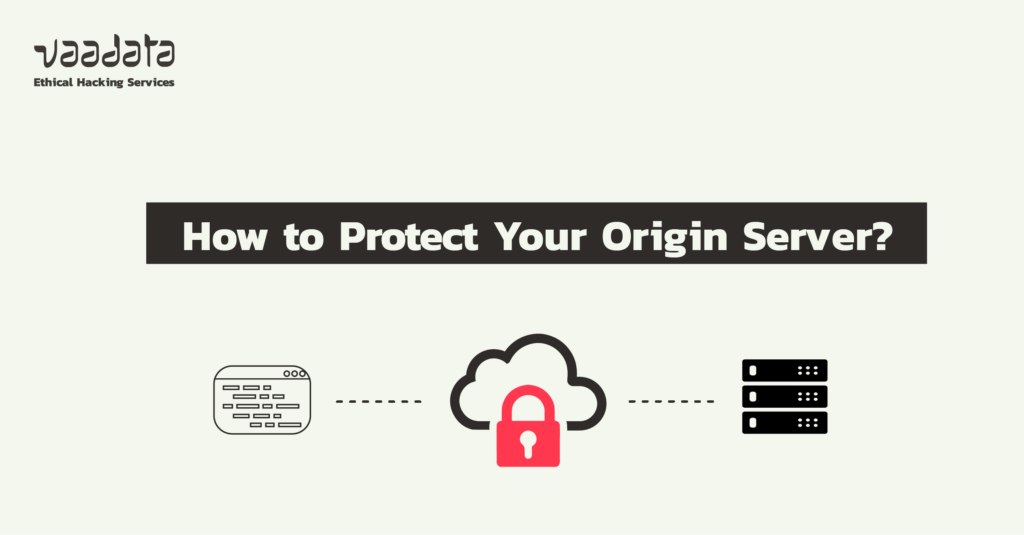
Cloudflare has established itself as a key player on the web in recent years, offering not only CDN services, but also protection against various attacks. However, for these protections to be fully effective, it is essential that the server is correctly configured.
Indeed, it is crucial to prevent attackers from gaining direct access to the servers hosting web applications. To do this, users must use Cloudflare, which will redirect traffic to the server according to the specific rules defined by the client.

Command injections are one of the most critical vulnerabilities in web security. They occur when an attacker manages to execute arbitrary system commands on the web server. This type of attack can result in the leakage of sensitive data, data corruption or complete control of the target environment.
In this article, we explore the principles and methods of command injection exploitation. We also present the security best practices and measures to implement to prevent these attacks.

Pre-Account Takeover is a type of attack that we very often carry out during our audits. Although it is only possible in very specific situations, the possibilities for malicious exploitation are becoming increasingly common, with potentially serious consequences for data security.
In this article, we present how a Pre-Account Takeover attack works. We will also look at the specifics of the attack, using a concrete example, as well as security best practices for countering the risk.

Security vulnerabilities are a major risk for modern web applications, potentially exposing sensitive user data and corporate infrastructures to malicious attacks.
One of the most feared vulnerabilities is Remote File Inclusion (RFI). This attack technique enables an attacker to inject and execute arbitrary code hosted on a remote server.



