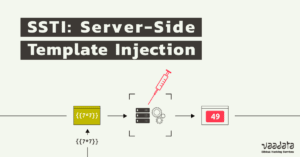
Server-side template injection (SSTI) vulnerabilities tend to be less researched than other types of flaws. However, their impact is significant and often leads to remote code execution (RCE). They are therefore flaws that should not be underestimated.
In what contexts do SSTI vulnerabilities occur? How to detect them and how to prevent them?
This is what we will see in this article.